- Apple
- 3M
- Samsung
- GE
- Microsoft
- Toyota
- P&G
- IBM
- Amazon
skip to main |
skip to sidebar

Leap Motion's not the household name Kinect is, but it should be — the company's motion-tracking system is more powerful, more accurate, smaller, cheaper, and just more impressive. Leap CTO David Holz came by the Verge's New York offices to give us a demo of the company's upcoming product (called The Leap), and suffice to say we're only begrudgingly returning to our mice and keyboards.
The Leap uses a number of camera sensors to map out a workspace of sorts — it's a 3D space in which you operate as you normally would, with almost none of the Kinect's angle and distance restrictions. Currently the Leap uses VGA camera sensors, and the workspace is about three cubic feet; Holz told us that bigger, better sensors are the only thing required to make that number more like thirty feet, or three hundred. Leap's device tracks all movement inside its force field, and is remarkably accurate, down to 0.01mm. It tracks your fingers individually, and knows the difference between your fingers and the pencil you're holding between two of them.
Holz showed off a number of different use cases for Leap Motion's technology. The simplest thing it can do is simulate a touch screen, so you can interact with any display as if it were touch-enabled — we were slicing pineapples in Fruit Ninja in seconds, without a moment of extra development or additional software.
Developers that do take advantage of the Leap's SDK will be able to do much more, however, and the possibilities appear to be limited only by your imagination. All kinds of different apps are being developed: some could improving remote surgery, others allow easier navigation through complex models and data, and others might put you square in the middle of a first-person shooter. It's like holding the Mario Kart steering wheel, but on a whole new level.
ather than mapping particular gestures (cross your arms to close the app, draw a circle to open a new window), Holz said developers are being encouraged to provide constant dynamic feedback. No one needed to be taught what pinch-to-zoom meant — it's the natural thing to try and do on a touchscreen, and as soon as you start pinching or spreading it becomes clear what happens. That's the paradigm for the Leap, Holz says: you should always be able to just do something, and the app or device should respond.
Leap Motion's plans are huge (Holz mentioned a few times wanting to totally upend traditional computing methods) but the company's playing its cards close. The Leap will cost $70 when it's released — sometime between December and February — and Leap Motion is also working with OEMs to embed its technology into devices. The Leap is about the size of a USB drive, but Holz says it could easily be no larger than a dime, so adding it to a laptop or tablet shouldn't be difficult.
Developers are apparently beating down the company's doors for access to the technology — Holz said thousands of Leaps will be given away in the next few months, before it's released to the public. That's no surprise: after only a few minutes of cutting fruit, scrolling around maps and webpages, and navigating through huge 3D spaces, all without ever touching a thing, we're pretty sure we've seen the next big thing in computing.
The natural comparison to any motion control is Minority Report, an imagined future everyone seems to desperately want to come true. We asked Holz about the comparison, and if Leap Motion's technology meant we'd all have Tom Cruise's awesome PreCrime dashboard in the future.
"No," he told us. "It'll be even better."

iPhone users whose devices have been stolen may soon get a little help from Apple when it comes to the problem of iMessages going to the pilfered phone. Ars has heard that Apple may be planning changes to the way iMessages are handled that will make it simpler for users to lock out unauthorized devices, though it's unclear when that might happen. In the meantime, some users are finding that there are some temporary "fixes" to the problem of iMessages going to stolen phones.
Ars covered this phenomenon last week when Ars reader David Hovis contacted us to tell us his wife's tale of woe. To recap: Mrs. Hovis' iPhone 4S was stolen, so she remotely wiped the device and then asked her carrier to deactivate the SIM. She then purchased a new iPhone and activated it with her old number—theoretically erasing all traces of her information from the original stolen phone. But when Hovis began sending iMessages to his wife, both she and the new owner of the stolen phone received them—Hovis and the new owner had a somewhat lengthy dialogue back and forth about the issue in order to confirm, and the new owner (who had allegedly purchased the stolen device from someone for $500) seemed just as perplexed as Hovis.
Several threads posted online recounted similar horror stories, and after publishing our piece, we received e-mails from a number of other affected users. One user who contacted us was deeply concerned that someone she knew as a stalker might have stolen her iPhone, and that all iMessages directed at her (on a new phone) were also going to the stalker. Clearly, this can turn into a major concern for some iPhone users.
I recommend reading Jesse Hollington's Google+ post (and the corresponding comments) on how to set a PIN on your SIM; it contains the default SIM codes for most of the popular carriers in the US and Canada. Please note that the SIM PIN trick won't work for Verizon iPhones—there is no SIM, and you can potentially lock yourself out much easier if you try to set a PIN for your nonexistent card. (Read the comment by Josh Schoenwald in the aforementioned Google+ post to find out what happens when you try to do this. Don't feel bad, Josh—you're helping everyone else learn!)
Still, our sources tell us that performing the aforementioned three-step process (remote wipe, deactivation, then activation on a new SIM) should work from this point on to lock out a stolen iPhone. So if you find yourself having some bad luck with thieves, it's worth trying that method before trying to set a PIN on your SIM card.
We'll keep you updated if and when we hear anything new about this issue, and please keep e-mailing me with your stories and observations about iMessage.

“I don’t want to say we’re making our own Facebook. But, we’re making our own Facebook,” said Ed Knutson, a web and mobile app developer who joined a team of activist-geeks redesigning social networking for the era of global protest.
They hope the technology they are developing can go well beyond Occupy Wall Street to help establish more distributed social networks, better online business collaboration and perhaps even add to the long-dreamed-of semantic web — an internet made not of messy text, but one unified by underlying meta-data that computers can easily parse.
The impetus is understandable. Social media helped pull together protesters around the globe in 2010 and 2011. Egyptian dictator Hosni Mubarak so feared Twitter and Facebook that he shut down Egypt’s internet service. A YouTube video posted in the name of Anonymous propelled Occupy Wall Street from an insider meme to national news. And top-trending Twitter hashtags turned Occupy from a ho-hum rally on Sept. 17 into a national and even international movement.
Now it’s time for activists to move beyond other people’s social networks and build their own, according to Knutson.
“We don’t want to trust Facebook with private messages among activists,” he said.
The same thinking applies to Twitter and other social networks — and the reasoning became clear last week, when a Massachusetts district attorney subpoenaed Twitter for information about the account @OccupyBoston and other accounts connected to the Boston movement. (To its credit, Twitter has a policy of giving users the opportunity to contest such orders when possible.)
“Those networks will be perfectly fine — until they are not. And it will be a one-day-to-the-next thing,” said Sam Boyer, an activist turned web developer, turned activist again, who works with the New York City occupation’s tech team.
A move away from mainstream social networks is already happening on several levels within the Occupy movements — from the local networks already set up for each occupation to an in-progress, overarching, international network project called Global Square, that Knutson is helping to build. Those networks are likely to be key to Occupy’s future, since nearly all of the largest encampments in the United States have been evicted — taking with them the physical spaces where activists communicated via the radically democratic General Assemblies.
The idea of an open alternative to corporate-owned social networking sites isn’t novel — efforts to build less centralized, open source alternatives to Facebook and Twitter have been in the works for years, with the best known examples being Diaspora and Identica.
But those developments aren’t specifically focused on protest movements. And the Occupy movement’s surprising rise in the U.S. has added new impetus to the desire for open source versions of the software that is playing an increasingly important role in mobilizing and connecting social movements, as well as broadcasting their efforts to the world.
One challenge that all of the new efforts face is a very difficult one for non-centralized services: ensuring that members are trustworthy. That’s critical for activists who risk injury and arrest in all countries and even death in some. To build trust, local and international networks will use a friend-of-a-friend model in Knutson and Boyer’s projects. People can’t become full members on their own as they can with social networks like Twitter, Facebook and Google+.
“You have to know someone in real life who sponsors you,” said Knutson.
To Boyer, it’s more important to identify someone as trustworthy than to ensure that their online name matches a passport or birth certificate.
“I respect pseudonyms as long as they treat them as pseudonyms and not as masks,” said Boyer. In other words, someone shouldn’t hide behind a fake name to get away with bad behavior — in an extreme case, infiltrating the movement to spy on or sabotage it.
Thirty-six-year-old Knutson, who lives in Milwaukee, Wisconsin, started the year as an observer of politics before evolving into a committed OWS activist. His metamorphosis started during public-employee strikes in February against proposed policies of Governor Scott Walker that would affect their benefits and collective-bargaining rights.
“Before this year we had the idea that things maybe were starting to improve a little,” he said. “But when things started happening in February we were like, ‘No, no. Things are getting worse.’”
While organizing a “Walkerville” protest camp in June, Knutson met, over Twitter, members of Spanish protest movement 15M. They had just built a web site, Take the Square, to track occupations around the world, from Tunisia to Madrid. He also met Alexa O’Brien – founder of campaign-finance-reform organization US Day of Rage and a co-founder of Occupy Wall Street. After OWS kicked off, Knutson came to the East Coast for a while, visiting New York, Boston and Philadelphia and joining with other techies in those cities.
Through all those connections, Knutson has focused on building the technology for an international occupations network. But the politics are tricky. “Some of the people in Spain are kind of resentful of OWS, because they got all of the credit,” he said, noting that the Spanish occupations started first and are still far bigger.
As a counterpart to Knutson, Sam Boyer focuses on the US occupations, building tech for a collection of interlinked social networks across the country with the working title Federated General Assembly, or FGA. Working on Occupy has brought him full-circle.
When he was an undergrad in 2005, Boyer, who is now 27, took a job at the Student Trade Justice Campaign, an organization focused on trade policy reform. In 2007, he wanted to build an online platform for individual chapters to organize into groups and to link those groups for national discussions – essentially what the FGA is meant to do. But Boyer couldn’t build it, he said. “I didn’t even know how to program at the point that I started with it.”
So Boyer started learning, and falling in love with, Web programming; and he switched from being mainly an activist to mainly an engineer. His specialty is an open-source content-management system for web sites called Drupal, which FGA will run on.
Knutson, Boyer and the other Occupy geeks don’t have to build everything from scratch. “These are standards that have been around for a while, and we are not reinventing the wheel,” said Boyer.
For instance, the projects will rely on set of technologies known as Open ID and OAuth that let a user sign into a new website using their logins and passwords from social networks like Facebook, Google and Twitter. Those technologies let you sign up for a new service by logging into a Twitter or Google account, which vouch for you to the new site without giving over your password or forcing you to get yet another username and password to keep track of.
In the new OWS tech, an activist’s local-occupation network can vouch for a user to another network, and the local networks all trust each other, they all trust that activist. Someone can sign into one network and post and comment on them all.
Some sensitive posts, say about civil disobedience, would be private. Others, like a statement of demands or press release, would be public, but only trusted members of the network could create them.
FGA wants to differentiate itself from the the me-me-me narcissism of Facebook. It has a strong focus on groups — working together on topics like alternative banking or electoral reform.
And there’s a lot of work today. Currently, the group aspects of Occupy web sites are a cacophony.
“You get there, and the first thing you look at is this useless activity feed,” said Boyer. Every comment – whether a brilliant idea, a troll comment or a me-too pile-on – pops into the list as it’s generated. “You’re only guaranteed that one person really thought that post was a good idea – not the whole group,” he said.
In the FGA system, each group has a discussion on what information to push to their home page, such as a description of an event, a blog post or minutes from a meeting. “In the same way that, when you look at Reddit, you know that the articles on top are the most upvoted, the user could know that posts appearing on a front page represent the concerted agreement of the group,” said Boyer.
The activist coders also want to be able to push and pull info to and from the rest of the movement. The idea is that they can have disparate systems that label info with shared tags that will, some day, make it possible to enter a search on any one site and pull precise results from around the world.
Ed Knutson’s job is to get those sites talking to each other, even though the content may be in different languages (English, Spanish, Arabic, etc.) and created with different content management systems, or CMSs, such as Drupal or Wordpress. The Global Square network will connect not through those systems but through “semantic Web” standards designed to link up disparate technologies.
One key standard has the wordy name Resource Description Framework, or RDF, a universal labeling system.
If an occupier wants to post the minutes of a meeting, for example, they might type them in the appropriate text box in the content management software running the site. That software pushes the information to an RDF database and tags it with some universal label – it could be called “minutes” or any other term that all the occupations agree on. The local occupier might also select “Group: Alternative Banking” from a dropdown list, and that label would be added as well. Using the same labels allows all the sites to trade information. So a search for minutes from an Alternative Banking group would pull up records from any occupation with that kind of group.
With RDF, sites can work together even if they run on different content management software, such as Drupal (as in the FGA) or Wordpress (as in the Spanish M15 group).
“The handoff point is that everything goes through RDF,” said Knutson. “You don’t care if they have a Drupal site or some kind of Frankenstein combination of different stuff.”
The problem the coders face will be the same one that’s faced the web for years – getting people to agree on standards and to then adopt them. One long-running attempt to do this quickly is called Microformats – a way of including markup data in HTML that’s invisible to an human visitor, but which can be understood by their browser or by a search engine. Examples include marking up contact information so that a reader can simply click contact information to add it to their address book and annotating a recipe so that search engines can let you search for recipes that include ’spinach’.
These linkage and collaboration capabilities would be useful well beyond the Occupy movement.
“I think any type of small or medium-sized group or a team that has one person in eight different cities,” could use it for collaboration, says Knutson. And he sees no reason against spinning off the tech to businesses.
“Every small and medium business owner is a member of the 99%,” said Knutson. “Furthermore, exploring relationships with businesses… is pretty important to having a tangible impact.”
“A lot of what we are tying to do is build a better conversation so that this cacophonous discussion can be more coordinated,” said Boyer. As an analogy, he recounted an OWS workshop from a conference on December 18 in New York City when the moderator asked everyone to shout out their best idea for the movement.
They were probably all good ideas, said Boyer. But he couldn’t hear any one of them through the noise of the others.
The Web of trust among networks, RDF labels that link data across occupations, working-group consensus on what to post – all are designed to help the right people connect to each other and to the right information. “Let the sheer number of people who are interested get out the way of the many things actually happening,” said Boyer.
But for now, all those ideas are just that – ideas. And whatever does emerge will come piecemeal.
Sam Boyer hopes to launch in the following weeks what he calls a stepping stone — a roster of occupations around the world called, for now, simply directory.occupy.net. M15’s Take the Square site has provided something like that since May, as have other sites. But directory.occupy.net will be unique in using RDF and other technologies to label all the entries. It will also allow people from each occupation to “own” and update their entries.
“The directory should be useful, but it’s not our big debut,” said Boyer. He’s hoping that will be sometime in the spring, when a rough version of the FGA social network launches.
The Global Square Knutson is helping to build is finalizing its tech and will launch, probably in January, with basic linkages for various Occupy sites to trade messages, re-publish articles and allow cross-commenting on them.
“I’d say it would be a pretty major accomplishment to get a couple of the [web site] systems that everyone is using, like ELGG and Drupal and media wiki and maybe Wordpress” to work together, he said.
But even just having the discussion has been a big deal. “It’s hard to get people to even think about that kind of stuff.”
Source-
Wired

To be eligible, it will exceed the 20,000 customers who are connected to the first phase and 750 000 for the second phase. This fiber will be drawn to a length of 300 km between Stockholm and Jönköping, thus taking all subscribers of this operator between the two cities. Telia is responsible for the fiber and equipment such as Cisco CRS-3, high-speed router that can handle up to 322 Tb / s.




 As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP. 1. Credit Card Frauds
As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP. 1. Credit Card Frauds
2. Bypass Website Country Restrictions
How Proxy Detection Works?
How to Tell Whether a given IP is Real or a Proxy?

So for all those who think that they can escape by using a spoofed IP, this post is the answer. I hope this information helps. Pass your comments.



Jobs resigned from the company, later telling an audience of Stanford University graduates "what had been the focus of my entire adult life was gone, and it was devastating." He would get the last laugh.

Tom Krazit, Erica Ogg, and Josh Lowensohn wrote this report.

(Credit: Daniel Terdiman/CNET)
 Mighty funny timing, Microsoft. Reports say that Google’s Chrome browser was threatening to overtake Firefox in the coming months thanks to soaring usage rates caused, in large part, by FF and IE defectors. Then, this morning, Internet forums are awash with rage because a new update to Microsoft’s Security Essentials and ForeFront AV software began calling Chrome a Trojan and erasing it from users machines. Coincidence? Yeah, it probably is. But that still doesn’t change the fact that users are pissed.
Mighty funny timing, Microsoft. Reports say that Google’s Chrome browser was threatening to overtake Firefox in the coming months thanks to soaring usage rates caused, in large part, by FF and IE defectors. Then, this morning, Internet forums are awash with rage because a new update to Microsoft’s Security Essentials and ForeFront AV software began calling Chrome a Trojan and erasing it from users machines. Coincidence? Yeah, it probably is. But that still doesn’t change the fact that users are pissed.
Both ZDNet and The Register are reporting that they’ve received numerous complaints about the critical false positive. The AV programs are identifying Chrome as part of the ZeuS Trojan, and users who try to reinstall the browser are finding that the antivirus program won’t let them, citing “PWS:Win32/Zbot” as a severe threat. Register readers are reporting that the beta version of Chrome isn’t affected, nor are browsers that are configured to not send Google any information. Nobody’s saying anything official at the moment – both Google and Microsoft have been mum on the matter.
So, has any of you been affected by the bug? Chime in with your experiences in the comments! I've got Chrome and MSE installed on my laptop, and nothing fishy has gone on yet.

 Sone days back Facebook announced Timeline, a crazy (and kind of creepy) omnibus look at everything that has ever happened in your Facebook lifespan. It’s like a story book of your life — or at least the online, documented parts.
Sone days back Facebook announced Timeline, a crazy (and kind of creepy) omnibus look at everything that has ever happened in your Facebook lifespan. It’s like a story book of your life — or at least the online, documented parts.
Facebook said that Timeline would be on the way for everyone sometime in the coming weeks… which is great and all, for everyone else. You’re the type of person who reads Borntohack, and are thus likely the type of person who likes their new and shiny things right now.
That’s okay. We can make it happen.
Fortunately, enabling Timeline a bit early isn’t too difficult — but it’s not at all straight forward, either.
You see, Facebook is enabling Timeline early for open graph developers. You, too, can be an open graph developer — even if you’re just looking to dabble.
A few things to note:
- You probably don’t want to do this unless you’re actually a developer. Expect bugs.
- Only you will see your timeline at first (unless you decide otherwise), but it will automatically go public after a few days. My timeline was automatically hard-set to go public on September 29th.
- It seems that if you login into Facebook on another machine, Timeline gets disabled automatically on all of your machines. With that said, it seems you can get back to your timeline (but ONLY after following the steps below) by navigating to http://www.facebook.com/YOURUSERNAMEHERE?sk=timeline
- You’ll need to have a “verified” account for one of the steps, which means you need a credit card or phone number attached to the account.
Here’s how to do it:
1. Log into Facebook
2. Enable developer mode, if you haven’t already. To do this, type “developer” into the Facebook search box, click the first result (it should be an app made by Facebook with a few hundred thousand users), and add the app.
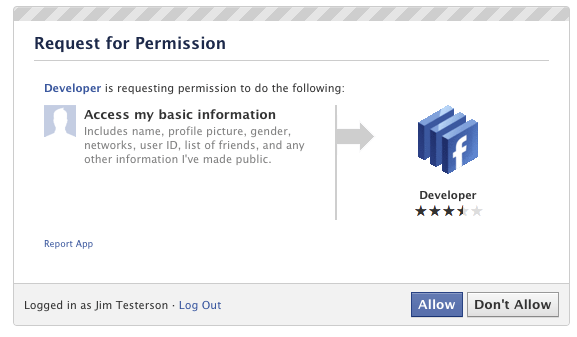
3. Jump into the developer app (if Facebook doesn’t put you there automatically, it should be in your left-hand tool bar)
4. Create a new app (don’t worry — you



- Find out what I'm doing, Follow Me :)
Showing posts with label Tech News. Show all posts
Showing posts with label Tech News. Show all posts
Saturday, April 27, 2013
List of Top 10 World’s Most Innovative Company in 2012:
Thursday, April 25, 2013
Most of Russian Shops Sell Pirated Microsoft Software
Microsoft found that approximately 25% of all Russian shops sell pirated copies of its software.Sellingand installing pirated Microsoft software is nothing short of an integral part of the mundane scenery inRussia, a study from the Redmond company found. Russian software outlets are easily getting away withcommercializing bootlegged products.
However, the market for dealing with unlicensed software is not as lucrative as it once was, as the retailers of counterfeit products face increasing risk of attracting the attention of authorities. “A few years ago most computer stores in some form or other offered pirate software,” revealed Denis Guz, head of the company’s department evangelizing the sale of licensed software, according to NZHerald. “Now, as we see, there are significantly fewer sales points of that kind … and now the majority of retailers offer only licensed programs.”
Microsoft’s study involved no less than 2,500 retail outlets in 53 Russian cities. The company found not only that one quarter of retailers was dealing with counterfeit copies of Microsoft Software, but that approximately 11% even went as far as to offer customers installation services.
Just as it did with all Central and East European markets, Microsoft is collaborating closely with Russian authorities in order to make sure that bootleggers of its software are brought to justice. Still, the process is slow and complex, and the Redmond company can hope to at least curb software piracy, but less to see the phenomenon stamped out.
What Is Software Piracy?
Software piracy is the mislicensing, unauthorized reproduction and illegal distribution of software, whether for business or personal use.
Software piracy is the mislicensing, unauthorized reproduction and illegal distribution of software, whether for business or personal use.
Impact Of Software Piracy
Pirated software hurts everyone—from software developers to retail store owners, and ultimately to allsoftware users. Furthermore, the illegal duplication and distribution of software has a significant impact on the economy.
Pirated software hurts everyone—from software developers to retail store owners, and ultimately to allsoftware users. Furthermore, the illegal duplication and distribution of software has a significant impact on the economy.
Wednesday, June 27, 2012
A look inLeaside Leap Motion, the 3D gesture control that's like Kinect on steroids

Leap Motion's not the household name Kinect is, but it should be — the company's motion-tracking system is more powerful, more accurate, smaller, cheaper, and just more impressive. Leap CTO David Holz came by the Verge's New York offices to give us a demo of the company's upcoming product (called The Leap), and suffice to say we're only begrudgingly returning to our mice and keyboards.
The Leap uses a number of camera sensors to map out a workspace of sorts — it's a 3D space in which you operate as you normally would, with almost none of the Kinect's angle and distance restrictions. Currently the Leap uses VGA camera sensors, and the workspace is about three cubic feet; Holz told us that bigger, better sensors are the only thing required to make that number more like thirty feet, or three hundred. Leap's device tracks all movement inside its force field, and is remarkably accurate, down to 0.01mm. It tracks your fingers individually, and knows the difference between your fingers and the pencil you're holding between two of them.
Holz showed off a number of different use cases for Leap Motion's technology. The simplest thing it can do is simulate a touch screen, so you can interact with any display as if it were touch-enabled — we were slicing pineapples in Fruit Ninja in seconds, without a moment of extra development or additional software.
Developers that do take advantage of the Leap's SDK will be able to do much more, however, and the possibilities appear to be limited only by your imagination. All kinds of different apps are being developed: some could improving remote surgery, others allow easier navigation through complex models and data, and others might put you square in the middle of a first-person shooter. It's like holding the Mario Kart steering wheel, but on a whole new level.
ather than mapping particular gestures (cross your arms to close the app, draw a circle to open a new window), Holz said developers are being encouraged to provide constant dynamic feedback. No one needed to be taught what pinch-to-zoom meant — it's the natural thing to try and do on a touchscreen, and as soon as you start pinching or spreading it becomes clear what happens. That's the paradigm for the Leap, Holz says: you should always be able to just do something, and the app or device should respond.
Leap Motion's plans are huge (Holz mentioned a few times wanting to totally upend traditional computing methods) but the company's playing its cards close. The Leap will cost $70 when it's released — sometime between December and February — and Leap Motion is also working with OEMs to embed its technology into devices. The Leap is about the size of a USB drive, but Holz says it could easily be no larger than a dime, so adding it to a laptop or tablet shouldn't be difficult.
Developers are apparently beating down the company's doors for access to the technology — Holz said thousands of Leaps will be given away in the next few months, before it's released to the public. That's no surprise: after only a few minutes of cutting fruit, scrolling around maps and webpages, and navigating through huge 3D spaces, all without ever touching a thing, we're pretty sure we've seen the next big thing in computing.
The natural comparison to any motion control is Minority Report, an imagined future everyone seems to desperately want to come true. We asked Holz about the comparison, and if Leap Motion's technology meant we'd all have Tom Cruise's awesome PreCrime dashboard in the future.
"No," he told us. "It'll be even better."
Sunday, January 29, 2012
Computer Coding: Not for Geeks Only
Credit: Business Week
The Web-based backlash against the Stop Online Piracy Act, a bill aimed at taking down overseas distributors of copyrighted movies and music, was much like the Internet itself: decentralized, anarchic, and powerful enough to help persuade Senate Majority Leader Harry Reid (D-Nev.) to shelve the bill on Jan. 20. There was no official slogan for the public pushback against perceived government meddling with the Web, but the unofficial one might have been a headline that appeared on the online magazine Motherboard: “Dear Congress, it’s no longer ok to not know how the Internet works.”
A growing number of people agree that not only should Congress understand how software is made, so should everyone. Designers, economists, doctors, and others with no direct connection to the technology world are embracing coding as a way to advance their careers, automate boring tasks, or just a means of self-improvement, a hobby like learning Spanish or doing crossword puzzles. And they have access to an expanding universe of free online coding tutorials from startups and universities such as Stanford and Massachusetts Institute of Technology. Programming is becoming “a much more fundamental piece of knowledge, similar to reading or writing,” says Andy Weissman, a partner at New York’s Union Square Venures, which led a $2.5 million investment round for Codecademy, a site that teaches people basic programming skills.
Source:
Saturday, December 31, 2011
iMessages going to stolen iPhones? There may be a fix in the works

iPhone users whose devices have been stolen may soon get a little help from Apple when it comes to the problem of iMessages going to the pilfered phone. Ars has heard that Apple may be planning changes to the way iMessages are handled that will make it simpler for users to lock out unauthorized devices, though it's unclear when that might happen. In the meantime, some users are finding that there are some temporary "fixes" to the problem of iMessages going to stolen phones.
Ars covered this phenomenon last week when Ars reader David Hovis contacted us to tell us his wife's tale of woe. To recap: Mrs. Hovis' iPhone 4S was stolen, so she remotely wiped the device and then asked her carrier to deactivate the SIM. She then purchased a new iPhone and activated it with her old number—theoretically erasing all traces of her information from the original stolen phone. But when Hovis began sending iMessages to his wife, both she and the new owner of the stolen phone received them—Hovis and the new owner had a somewhat lengthy dialogue back and forth about the issue in order to confirm, and the new owner (who had allegedly purchased the stolen device from someone for $500) seemed just as perplexed as Hovis.
Several threads posted online recounted similar horror stories, and after publishing our piece, we received e-mails from a number of other affected users. One user who contacted us was deeply concerned that someone she knew as a stalker might have stolen her iPhone, and that all iMessages directed at her (on a new phone) were also going to the stalker. Clearly, this can turn into a major concern for some iPhone users.
The "fixes"
So what is a worried iPhone user to do to protect yourself? There's a growing consensus that there are indeed some ways to prevent iMessages from going to the wrong place, though some of the proposed solutions directly conflict with what some of the affected users have told Ars. Our friends at Macworld posted an article on Thursday claiming that a simple three-step process should help prevent this from happening:Macworld can confirm that perhaps the easiest way to ensure that a stolen phone stops receiving iMessages is to remotely wipe the phone, and then call your carrier and instruct them to deactivate your old SIM. The third and final step? Activate a new SIM in your new phone.We were unable to test this ourselves, so we're taking Macworld at their word—I spoke with the author of the piece, Lex Friedman, who told me he tested it personally with success. I went back to speak with Hovis with this article in hand, however, and he told me that he performed those same steps in the same order without success—the messages still went through to the owner of the stolen phone. Our only guess is that Apple has already made some changes to iMessage on the server side between the time Hovis performed his remote wipe and the time Friedman performed his remote wipe, but this remains unconfirmed.
Completing those three steps—wiping, deactivating your old SIM, and then activating a new one—ensures that your iMessages will get sent only to you and your iOS devices, and not anywhere else.
Setting a SIM PIN
There is another, slightly more complicated process that will also work to lock out stolen iPhones from your iMessages, but be warned: it could also block you from finding the phone via Find My iPhone if the thief reboots your phone. You can set a PIN on your SIM card, which is different than setting a PIN for the phone. The reason this is a less-ideal solution isn't just because it's more complicated—it's also because each carrier already has a default PIN set for your SIM card, and you risk locking yourself out from your own account if you don't do this correctly.I recommend reading Jesse Hollington's Google+ post (and the corresponding comments) on how to set a PIN on your SIM; it contains the default SIM codes for most of the popular carriers in the US and Canada. Please note that the SIM PIN trick won't work for Verizon iPhones—there is no SIM, and you can potentially lock yourself out much easier if you try to set a PIN for your nonexistent card. (Read the comment by Josh Schoenwald in the aforementioned Google+ post to find out what happens when you try to do this. Don't feel bad, Josh—you're helping everyone else learn!)
Still, our sources tell us that performing the aforementioned three-step process (remote wipe, deactivation, then activation on a new SIM) should work from this point on to lock out a stolen iPhone. So if you find yourself having some bad luck with thieves, it's worth trying that method before trying to set a PIN on your SIM card.
We'll keep you updated if and when we hear anything new about this issue, and please keep e-mailing me with your stories and observations about iMessage.
Source:
Friday, December 30, 2011
Occupy Geeks Are Building a Facebook for the 99%

Protesters volunteering for the internet and information boards of the Occupy Wall Street protest work and broadcast from their media center in Zuccotti Plaza on Oct. 2, 2011. Photo: Bryan Derballa for Wired.com
“I don’t want to say we’re making our own Facebook. But, we’re making our own Facebook,” said Ed Knutson, a web and mobile app developer who joined a team of activist-geeks redesigning social networking for the era of global protest.
They hope the technology they are developing can go well beyond Occupy Wall Street to help establish more distributed social networks, better online business collaboration and perhaps even add to the long-dreamed-of semantic web — an internet made not of messy text, but one unified by underlying meta-data that computers can easily parse.
The impetus is understandable. Social media helped pull together protesters around the globe in 2010 and 2011. Egyptian dictator Hosni Mubarak so feared Twitter and Facebook that he shut down Egypt’s internet service. A YouTube video posted in the name of Anonymous propelled Occupy Wall Street from an insider meme to national news. And top-trending Twitter hashtags turned Occupy from a ho-hum rally on Sept. 17 into a national and even international movement.
Now it’s time for activists to move beyond other people’s social networks and build their own, according to Knutson.
“We don’t want to trust Facebook with private messages among activists,” he said.
The same thinking applies to Twitter and other social networks — and the reasoning became clear last week, when a Massachusetts district attorney subpoenaed Twitter for information about the account @OccupyBoston and other accounts connected to the Boston movement. (To its credit, Twitter has a policy of giving users the opportunity to contest such orders when possible.)
“Those networks will be perfectly fine — until they are not. And it will be a one-day-to-the-next thing,” said Sam Boyer, an activist turned web developer, turned activist again, who works with the New York City occupation’s tech team.
A move away from mainstream social networks is already happening on several levels within the Occupy movements — from the local networks already set up for each occupation to an in-progress, overarching, international network project called Global Square, that Knutson is helping to build. Those networks are likely to be key to Occupy’s future, since nearly all of the largest encampments in the United States have been evicted — taking with them the physical spaces where activists communicated via the radically democratic General Assemblies.
The idea of an open alternative to corporate-owned social networking sites isn’t novel — efforts to build less centralized, open source alternatives to Facebook and Twitter have been in the works for years, with the best known examples being Diaspora and Identica.
But those developments aren’t specifically focused on protest movements. And the Occupy movement’s surprising rise in the U.S. has added new impetus to the desire for open source versions of the software that is playing an increasingly important role in mobilizing and connecting social movements, as well as broadcasting their efforts to the world.
One challenge that all of the new efforts face is a very difficult one for non-centralized services: ensuring that members are trustworthy. That’s critical for activists who risk injury and arrest in all countries and even death in some. To build trust, local and international networks will use a friend-of-a-friend model in Knutson and Boyer’s projects. People can’t become full members on their own as they can with social networks like Twitter, Facebook and Google+.
“You have to know someone in real life who sponsors you,” said Knutson.
To Boyer, it’s more important to identify someone as trustworthy than to ensure that their online name matches a passport or birth certificate.
“I respect pseudonyms as long as they treat them as pseudonyms and not as masks,” said Boyer. In other words, someone shouldn’t hide behind a fake name to get away with bad behavior — in an extreme case, infiltrating the movement to spy on or sabotage it.
Thirty-six-year-old Knutson, who lives in Milwaukee, Wisconsin, started the year as an observer of politics before evolving into a committed OWS activist. His metamorphosis started during public-employee strikes in February against proposed policies of Governor Scott Walker that would affect their benefits and collective-bargaining rights.
“Before this year we had the idea that things maybe were starting to improve a little,” he said. “But when things started happening in February we were like, ‘No, no. Things are getting worse.’”
While organizing a “Walkerville” protest camp in June, Knutson met, over Twitter, members of Spanish protest movement 15M. They had just built a web site, Take the Square, to track occupations around the world, from Tunisia to Madrid. He also met Alexa O’Brien – founder of campaign-finance-reform organization US Day of Rage and a co-founder of Occupy Wall Street. After OWS kicked off, Knutson came to the East Coast for a while, visiting New York, Boston and Philadelphia and joining with other techies in those cities.
Through all those connections, Knutson has focused on building the technology for an international occupations network. But the politics are tricky. “Some of the people in Spain are kind of resentful of OWS, because they got all of the credit,” he said, noting that the Spanish occupations started first and are still far bigger.
As a counterpart to Knutson, Sam Boyer focuses on the US occupations, building tech for a collection of interlinked social networks across the country with the working title Federated General Assembly, or FGA. Working on Occupy has brought him full-circle.
When he was an undergrad in 2005, Boyer, who is now 27, took a job at the Student Trade Justice Campaign, an organization focused on trade policy reform. In 2007, he wanted to build an online platform for individual chapters to organize into groups and to link those groups for national discussions – essentially what the FGA is meant to do. But Boyer couldn’t build it, he said. “I didn’t even know how to program at the point that I started with it.”
So Boyer started learning, and falling in love with, Web programming; and he switched from being mainly an activist to mainly an engineer. His specialty is an open-source content-management system for web sites called Drupal, which FGA will run on.
Knutson, Boyer and the other Occupy geeks don’t have to build everything from scratch. “These are standards that have been around for a while, and we are not reinventing the wheel,” said Boyer.
For instance, the projects will rely on set of technologies known as Open ID and OAuth that let a user sign into a new website using their logins and passwords from social networks like Facebook, Google and Twitter. Those technologies let you sign up for a new service by logging into a Twitter or Google account, which vouch for you to the new site without giving over your password or forcing you to get yet another username and password to keep track of.
In the new OWS tech, an activist’s local-occupation network can vouch for a user to another network, and the local networks all trust each other, they all trust that activist. Someone can sign into one network and post and comment on them all.
Some sensitive posts, say about civil disobedience, would be private. Others, like a statement of demands or press release, would be public, but only trusted members of the network could create them.
FGA wants to differentiate itself from the the me-me-me narcissism of Facebook. It has a strong focus on groups — working together on topics like alternative banking or electoral reform.
And there’s a lot of work today. Currently, the group aspects of Occupy web sites are a cacophony.
“You get there, and the first thing you look at is this useless activity feed,” said Boyer. Every comment – whether a brilliant idea, a troll comment or a me-too pile-on – pops into the list as it’s generated. “You’re only guaranteed that one person really thought that post was a good idea – not the whole group,” he said.
In the FGA system, each group has a discussion on what information to push to their home page, such as a description of an event, a blog post or minutes from a meeting. “In the same way that, when you look at Reddit, you know that the articles on top are the most upvoted, the user could know that posts appearing on a front page represent the concerted agreement of the group,” said Boyer.
The activist coders also want to be able to push and pull info to and from the rest of the movement. The idea is that they can have disparate systems that label info with shared tags that will, some day, make it possible to enter a search on any one site and pull precise results from around the world.
Ed Knutson’s job is to get those sites talking to each other, even though the content may be in different languages (English, Spanish, Arabic, etc.) and created with different content management systems, or CMSs, such as Drupal or Wordpress. The Global Square network will connect not through those systems but through “semantic Web” standards designed to link up disparate technologies.
One key standard has the wordy name Resource Description Framework, or RDF, a universal labeling system.
If an occupier wants to post the minutes of a meeting, for example, they might type them in the appropriate text box in the content management software running the site. That software pushes the information to an RDF database and tags it with some universal label – it could be called “minutes” or any other term that all the occupations agree on. The local occupier might also select “Group: Alternative Banking” from a dropdown list, and that label would be added as well. Using the same labels allows all the sites to trade information. So a search for minutes from an Alternative Banking group would pull up records from any occupation with that kind of group.
With RDF, sites can work together even if they run on different content management software, such as Drupal (as in the FGA) or Wordpress (as in the Spanish M15 group).
“The handoff point is that everything goes through RDF,” said Knutson. “You don’t care if they have a Drupal site or some kind of Frankenstein combination of different stuff.”
The problem the coders face will be the same one that’s faced the web for years – getting people to agree on standards and to then adopt them. One long-running attempt to do this quickly is called Microformats – a way of including markup data in HTML that’s invisible to an human visitor, but which can be understood by their browser or by a search engine. Examples include marking up contact information so that a reader can simply click contact information to add it to their address book and annotating a recipe so that search engines can let you search for recipes that include ’spinach’.
These linkage and collaboration capabilities would be useful well beyond the Occupy movement.
“I think any type of small or medium-sized group or a team that has one person in eight different cities,” could use it for collaboration, says Knutson. And he sees no reason against spinning off the tech to businesses.
“Every small and medium business owner is a member of the 99%,” said Knutson. “Furthermore, exploring relationships with businesses… is pretty important to having a tangible impact.”
“A lot of what we are tying to do is build a better conversation so that this cacophonous discussion can be more coordinated,” said Boyer. As an analogy, he recounted an OWS workshop from a conference on December 18 in New York City when the moderator asked everyone to shout out their best idea for the movement.
They were probably all good ideas, said Boyer. But he couldn’t hear any one of them through the noise of the others.
The Web of trust among networks, RDF labels that link data across occupations, working-group consensus on what to post – all are designed to help the right people connect to each other and to the right information. “Let the sheer number of people who are interested get out the way of the many things actually happening,” said Boyer.
But for now, all those ideas are just that – ideas. And whatever does emerge will come piecemeal.
Sam Boyer hopes to launch in the following weeks what he calls a stepping stone — a roster of occupations around the world called, for now, simply directory.occupy.net. M15’s Take the Square site has provided something like that since May, as have other sites. But directory.occupy.net will be unique in using RDF and other technologies to label all the entries. It will also allow people from each occupation to “own” and update their entries.
“The directory should be useful, but it’s not our big debut,” said Boyer. He’s hoping that will be sometime in the spring, when a rough version of the FGA social network launches.
The Global Square Knutson is helping to build is finalizing its tech and will launch, probably in January, with basic linkages for various Occupy sites to trade messages, re-publish articles and allow cross-commenting on them.
“I’d say it would be a pretty major accomplishment to get a couple of the [web site] systems that everyone is using, like ELGG and Drupal and media wiki and maybe Wordpress” to work together, he said.
But even just having the discussion has been a big deal. “It’s hard to get people to even think about that kind of stuff.”
Source-
Wired
Thursday, December 29, 2011
RSA's Art Coviello predicts 2012 to be the year of resiliency and adaptation

Credit: Wikipedia
RSA executive chairman Art Coviello said that if 2011 was the year of the attack, then 2012 will be the year of resiliency and adaptation within the industry.
In an open letter, Coviello said the company's experiences of this year "have indeed made us stronger and smarter".
“Our society has made unimaginable progress over the past 20 years through advances in information technology. It's our responsibility to sustain this advancement through a trusted digital world,” he said. He added that never in his career has he known CEOs and corporate boards to be as interested in security as they are now; and he cited one common theme: persistent, advanced and intelligent threats.
In an open letter, Coviello said the company's experiences of this year "have indeed made us stronger and smarter".
“Our society has made unimaginable progress over the past 20 years through advances in information technology. It's our responsibility to sustain this advancement through a trusted digital world,” he said. He added that never in his career has he known CEOs and corporate boards to be as interested in security as they are now; and he cited one common theme: persistent, advanced and intelligent threats.
Friday, December 23, 2011
In Sweden, the Fiber optic up to 120 GBPS.....!!!!
In Sweden, a new record is being built around fiber optic ...
In Sweden, a scale experiment is taking place right now. Cisco and Telia (Swedish ISP) test a fiber network to go up to 120 Gbps! They even made an application for deposit in the Guinness Book to be recognized as the largest LAN parties in the world ...
To be eligible, it will exceed the 20,000 customers who are connected to the first phase and 750 000 for the second phase. This fiber will be drawn to a length of 300 km between Stockholm and Jönköping, thus taking all subscribers of this operator between the two cities. Telia is responsible for the fiber and equipment such as Cisco CRS-3, high-speed router that can handle up to 322 Tb / s.
Both partners explain that if the test is successful, it will be a new record for the networks and a new perspective for the use of new technologies. This will allow the 750,000 lucky to eg download a movie in high definition (legally, of course) in just 0.05 seconds! Subscribers' computers, however, should become limiting factors, the world upside down?!
And we, during that time, we dream of the widespread 100 Mbps FTTH throughout ...
And we, during that time, we dream of the widespread 100 Mbps FTTH throughout ...
Wednesday, November 23, 2011
Mobile Devices, Virtualization Are Biggest Security Challenges

Credit: Wayan Vota (Flickr)
Increased use of mobile devices, especially smartphones, in addition to the transition to virtualization, are key factors weighing on enterprises trying to sort out security strategy and budgets, according to a survey of 688 information and security managers.
According to the Ponemon Institute's "State of the Endpoint" study released this week, there are serious signs that IT operations and IT security often fail to work as a team. Forty percent say collaboration is "poor or non-existent" and 48% call it "adequate, but can be improved." Virtualization, mainly VMware and Microsoft Hyper-V, are increasingly the software platforms their organizations support, and 55% say virtualization does require "additional security measures," with most turning for help with that to the virtualization vendor or vendors with specialized virtualization security components.
But a surprising 41% indicated responsibility for virtualization security isn't clearly defined by department or function. Additionally, 21% said IT security was responsible, 15% said IT operations was and 11% said it was the job for IT compliance. Mobile devices - especially the use of employee-owned devices for work purposes - are also putting new stress on the IT department, according to the survey, which was sponsored by Lumension. The survey shows that mobile devices, especially smartphones, are counted as among "the greatest rise of potential IT security risk."
According to the Ponemon Institute's "State of the Endpoint" study released this week, there are serious signs that IT operations and IT security often fail to work as a team. Forty percent say collaboration is "poor or non-existent" and 48% call it "adequate, but can be improved." Virtualization, mainly VMware and Microsoft Hyper-V, are increasingly the software platforms their organizations support, and 55% say virtualization does require "additional security measures," with most turning for help with that to the virtualization vendor or vendors with specialized virtualization security components.
But a surprising 41% indicated responsibility for virtualization security isn't clearly defined by department or function. Additionally, 21% said IT security was responsible, 15% said IT operations was and 11% said it was the job for IT compliance. Mobile devices - especially the use of employee-owned devices for work purposes - are also putting new stress on the IT department, according to the survey, which was sponsored by Lumension. The survey shows that mobile devices, especially smartphones, are counted as among "the greatest rise of potential IT security risk."
Source:
Tuesday, November 22, 2011
Why do companies backup infrequently?

Credit: Brian J. Matis (Flickr)
Businesses are on average backing up to tape once a month, with one rather alarming statistic from the same survey showing 10 percent were only backing up to tape once per year, according to a survey by Vanson Bourne.
Although cloud backup solutions are becoming more common, still the majority of companies will do their backups in-house. Sometimes they will have dedicated IT staff to run them, but usually it's done in-house because they have always done it like that, and they have confidence in their own security and safekeeping of data.
Given this fact that IT personal are perhaps creatures of habit, and wouldn't risk a cloud based back-up solution - due to security and/or data integrity - it then seems a little odd that backups are done as infrequently as the survey reveals or even that they are only done once per year by some companies. The likely reason for this infrequency is due to the time factor involved. Many companies would run their backups on Friday evenings, in the hope for it to be completed by Monday business start. But with such large data pools, these backups might not complete in time, and are therefore often postponed for larger time frame windows.
Although cloud backup solutions are becoming more common, still the majority of companies will do their backups in-house. Sometimes they will have dedicated IT staff to run them, but usually it's done in-house because they have always done it like that, and they have confidence in their own security and safekeeping of data.
Given this fact that IT personal are perhaps creatures of habit, and wouldn't risk a cloud based back-up solution - due to security and/or data integrity - it then seems a little odd that backups are done as infrequently as the survey reveals or even that they are only done once per year by some companies. The likely reason for this infrequency is due to the time factor involved. Many companies would run their backups on Friday evenings, in the hope for it to be completed by Monday business start. But with such large data pools, these backups might not complete in time, and are therefore often postponed for larger time frame windows.
Sunday, November 13, 2011
Siri hacked to work on iPhone 3GS

Credit: Cult of Mac
We recently told you about the hidden panorama mode in the iOS 5 Camera app that could be enabled by editing a .plist file. Since then, a jailbreak tweak called “Firebreak” has been released that automatically enables the feature on any jailbroken iOS 5 device.
Panorama mode in the iOS Camera actually works, and you can get it on your own device right now without jailbreaking.
A simple hack has surfaced that enables the hidden panorama mode on the iPhone 4S, iPhone 4, iPod touch, and iPad 2 running iOS 5. To enable the feature, you’ll need to perform a modified backup of your iOS device in iTunes. You will also need to restore from a new backup, so keep that in mind before continuing.
Panorama mode in the iOS Camera actually works, and you can get it on your own device right now without jailbreaking.
A simple hack has surfaced that enables the hidden panorama mode on the iPhone 4S, iPhone 4, iPod touch, and iPad 2 running iOS 5. To enable the feature, you’ll need to perform a modified backup of your iOS device in iTunes. You will also need to restore from a new backup, so keep that in mind before continuing.
Source:
Labels:
apple,
Born To Hack,
hacks,
iPhone,
IPod Stuff,
Master Of All Hacking Warez,
Mehta,
Shaify,
Shaify Borntohack,
Shaify master of all hacking warez,
Shaify Mehta,
shaify.com,
Tech News
Friday, November 11, 2011
Poor wi-fi? Cook up a better signal with a baking tray

Credit: silicon.com
No matter how well prepared you are, there are times when you don't quite have to hand all the technology you really need.
Today, I find myself on a boat in just that situation and unable to get online with wi-fi or 2.5G for want of a better antenna. My mobile phone is showing one bar of 2.5G and one bar of wi-fi. My laptop isn't doing any better, and a data connection is proving impossible.
There are some buildings behind the trees on the other side of the river, and my scanner is showing a number of open access wi-fi opportunities. But all I have is what I carry, and that does not include a high-gain antenna. Time to improvise. A visit to the galley turns up a much-used baking tray. A few simple experiments later and I'm able to locate the direction of the 2.5G base station and the strongest wi-fi signal.
Today, I find myself on a boat in just that situation and unable to get online with wi-fi or 2.5G for want of a better antenna. My mobile phone is showing one bar of 2.5G and one bar of wi-fi. My laptop isn't doing any better, and a data connection is proving impossible.
There are some buildings behind the trees on the other side of the river, and my scanner is showing a number of open access wi-fi opportunities. But all I have is what I carry, and that does not include a high-gain antenna. Time to improvise. A visit to the galley turns up a much-used baking tray. A few simple experiments later and I'm able to locate the direction of the 2.5G base station and the strongest wi-fi signal.
Source:
Wednesday, November 9, 2011
How to Detect Anonymous IP Addresses
 As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.
As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.For example, say a Nigerian fraudster tries to purchase goods online with a stolen credit card for which the billing address is associated with New York. Most credit card merchants use Geo-location to block orders from countries like Nigeria and other high risk countries. So in order to bypass this restriction the credit card fraudster uses a proxy to spoof his IP address so that it appears to have come from New York. The IP address location appears to be legitimate since it is in the same city as the billing address. A proxy check would be needed to flag this order.
Some website services are restricted to users form only a selected list of countries. For example, a paid survey may be restricted only to countries like United States and Canada. So a user from say China may use a proxy so as to make his IP appear to have come from U.S. so that he can earn from participating in the paid survey.
Proxy Detection Services
So in order to stop such online frauds, Proxy Detection has become a critical component. Today most companies, credit card merchants and websites that deal with e-commerce transactions make use of Proxy Detection Services like MaxMind and FraudLabs to detect the usage of proxy or spoofed IP from users participating online.
Proxy Detection web services allow instant detection of anonymous IP addresses. Even though the use of proxy address by users is not a direct indication of fraudulent behaviour, it can often indicate the intention of the user to hide his or her real IP. In fact, some of the most used ISPs like AOL and MSN are forms of proxies and are used by both good and bad consumers.
Proxy detection services often rely on IP addresses to determine whether or not the IP is a proxy. Merchants can obtain the IP address of the users from the HTTP header on the order that comes into their website. This IP address is sent to the proxy detecting service in real time to confirm it’s authenticity.
The proxy detection services on the other hand compare this IP against a known list of flagged IPs that belong to proxy services. If the IP is not on the list then it is authenticated and the confirmation is sent back to the merchant. Otherwise it is reported to be a suspected proxy. These proxy detection services work continuously to grab a list or range of IPs that are commonly used for proxy services. With this it is possible to tell whether or not a given IP address is a proxy or spoofed IP.
There are a few free sites that help you determine whether or not a given IP is a proxy. You can use free services like WhatisMyIPAddress to detect proxy IPs. Just enter the suspected IP in the field and click on “Lookup IP Address” button to check the IP address. If it is a suspected proxy then you will see the results something as follows.

So for all those who think that they can escape by using a spoofed IP, this post is the answer. I hope this information helps. Pass your comments.
What is CAPTCHA and How it Works?
CAPTCHA or Captcha (pronounced as cap-ch-uh) which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart” is a type of challenge-response test to ensure that the response is only generated by humans and not by a computer. In simple words, CAPTCHA is the word verification test that you will come across the end of a sign-up form while signing up for Gmail or Yahoo account. The following image shows the typical samples of CAPTCHA.

Almost every Internet user will have an experience of CAPTCHA in their daily Internet usage, but only a few are aware of what it is and why they are used. So in this post you will find a detailed information on how CAPTCHA works and why they are used.
What Purpose does CAPTCHA Exactly Serve?
CAPTCPA is mainly used to prevent automated software (bots) from performing actions on behalf of actual humans. For example while signing up for a new email account, you will come across a CAPTCHA at the end of the sign-up form so as to ensure that the form is filled out only by a legitimate human and not by any of the automated software or a computer bot. The main goal of CAPTCHA is to put forth a test which is simple and straight forward for any human to answer but for a computer, it is almost impossible to solve.
What is the Need to Create a Test that Can Tell Computers and Humans Apart?
For many the CAPTCHA may seem to be silly and annoying, but in fact it has the ability to protect systems from malicious attacks where people try to game the system. Attackers can make use of automated softwares to generate a huge quantity of requests thereby causing a high load on the target server which would degrade the quality of service of a given system, whether due to abuse or resource expenditure. This can affect millions of legitimate users and their requests. CAPTCHAs can be deployed to protect systems that are vulnerable to email spam, such as the services from Gmail, Yahoo and Hotmail.
Who Uses CAPTCHA?
CAPTCHAs are mainly used by websites that offer services like online polls and registration forms. For example, Web-based email services like Gmail, Yahoo and Hotmail offer free email accounts for their users. However upon each sign-up process, CAPTCHAs are used to prevent spammers from using a bot to generate hundreds of spam mail accounts.
Designing a CAPTCHA System
CAPTCHAs are designed on the fact that computers lack the ability that human beings have when it comes to processing visual data. It is more easily possible for humans to look at an image and pick out the patterns than a computer. This is because computers lack the real intelligence that humans have by default. CAPTCHAs are implemented by presenting users with an image which contains distorted or randomly stretched characters which only humans should be able to identify. Sometimes characters are striked out or presented with a noisy background to make it even more harder for computers to figure out the patterns.
Most, but not all, CAPTCHAs rely on a visual test. Some Websites implement a totally different CAPTCHA system to tell humans and computers apart. For example, a user is presented with 4 images in which 3 contains picture of animals and one contain a flower. The user is asked to select only those images which contain animals in them. This Turing test can easily be solved by any human, but almost impossible for a computer.
Breaking the CAPTCHA
The challenge in breaking the CAPTCHA lies in real hard task of teaching a computer how to process information in a way similar to how humans think. Algorithms with artificial intelligence (AI) will have to be designed in order to make the computer think like humans when it comes to recognizing the patterns in images. However there is no universal algorithm that could pass through and break any CAPTCHA system and hence each CAPTCHA algorithm must have to be tackled individually. It might not work 100 percent of the time, but it can work often enough to be worthwhile to spammers.
Wednesday, October 12, 2011
You can now use iCloud: Its free
Apple devices can be addictive: People buy one tiny iPod, fall in love, and end up with three or four other Apple products. Now if only they could see all their data on all those devices simultaneously.
Starting today, they can.

Thanks to iCloud, the iPhone, iPad and iPod Touch all have the same document with no work on the user’s part.
ICloud is designed to store and replicate documents, music, apps and 1,000 photos on PCs, the iPhone, iPod Touch and iPad. It also syncs contacts, calendars and email so all your machines and devices have the same data and content. It will back up five gigabytes of data, but certain types aren’t counted against that total. The best part: It’s free.
I’ve been testing iCloud’s sync ability between a MacBook Pro, iPhone 4S and iPad 3G. I also accessed and added content using iCloud.com. At first, I ran into a few hiccups with syncing photos, but an Apple spokesman explained that the company’s servers were occasionally down while they were being prepared for Wednesday’s iCloud launch. After that, iCloud worked without a hitch—well enough that I stopped thinking about which device held what since they were all updated with the same content.
On the downside, iCloud doesn’t automatically sync videos to other devices. In WiFi, it won’t sync edited photos if edits are made on a device after its camera app is closed. (This includes removing red eye, cropping and auto-enhancing images.) And document sharing on iCloud is focused on sharing with oneself, not with other people, unlike the document-sharing solutions from Google and Microsoft.
I found iCloud’s most useful feature to be Photo Stream, which automatically sends images captured by an iPhone, iPad and iPod Touch up to iCloud and replicates them on all other iCloud devices, one by one. Watching these photos pop onto the screen of my computer, iPad or iPhone was nothing short of delightful.
Photos are pushed via iCloud to the Mac and PC in their full resolution and sent to the iPad, iPod Touch or iPhone in a resolution that’s optimized for those displays.

Photo Stream sends images captured by mobile devices, such as the iPhone and iPad, up to iCloud and replicates them on all other iCloud devices,
By default, any images imported to a PC or Mac are automatically sent into Photo Stream, though this setting can be turned off. Devices need only be powered on and in WiFi to receive images from Photo Stream.
Each photo remains in Photo Stream for
Starting today, they can.

Thanks to iCloud, the iPhone, iPad and iPod Touch all have the same document with no work on the user’s part.
ICloud is designed to store and replicate documents, music, apps and 1,000 photos on PCs, the iPhone, iPod Touch and iPad. It also syncs contacts, calendars and email so all your machines and devices have the same data and content. It will back up five gigabytes of data, but certain types aren’t counted against that total. The best part: It’s free.
I’ve been testing iCloud’s sync ability between a MacBook Pro, iPhone 4S and iPad 3G. I also accessed and added content using iCloud.com. At first, I ran into a few hiccups with syncing photos, but an Apple spokesman explained that the company’s servers were occasionally down while they were being prepared for Wednesday’s iCloud launch. After that, iCloud worked without a hitch—well enough that I stopped thinking about which device held what since they were all updated with the same content.
On the downside, iCloud doesn’t automatically sync videos to other devices. In WiFi, it won’t sync edited photos if edits are made on a device after its camera app is closed. (This includes removing red eye, cropping and auto-enhancing images.) And document sharing on iCloud is focused on sharing with oneself, not with other people, unlike the document-sharing solutions from Google and Microsoft.
I found iCloud’s most useful feature to be Photo Stream, which automatically sends images captured by an iPhone, iPad and iPod Touch up to iCloud and replicates them on all other iCloud devices, one by one. Watching these photos pop onto the screen of my computer, iPad or iPhone was nothing short of delightful.
Photos are pushed via iCloud to the Mac and PC in their full resolution and sent to the iPad, iPod Touch or iPhone in a resolution that’s optimized for those displays.

Photo Stream sends images captured by mobile devices, such as the iPhone and iPad, up to iCloud and replicates them on all other iCloud devices,
By default, any images imported to a PC or Mac are automatically sent into Photo Stream, though this setting can be turned off. Devices need only be powered on and in WiFi to receive images from Photo Stream.
Each photo remains in Photo Stream for
Thursday, October 6, 2011
Apple co-founder, Chairman Steve Jobs dies

Steve Jobs introducing the iPhone 4 last year.
(Credit: James Martin/CNET)Apple co-founder and Chairman Steve Jobs died today, Apple said. He was 56.
"Steve's brilliance, passion and energy were the source of countless innovations that enrich and improve all of our lives," Apple said in a statement. "The world is immeasurably better because of Steve."
Jobs had been suffering from various health issues following the seventh anniversary of his surgery for a rare form of pancreatic cancer in August 2004. Apple announced in January that he would be taking an indeterminate medical leave of absence, with Jobs then stepping down from his role as CEO in late August.
Jobs had undergone a liver transplant in April 2009 during an earlier planned six-month leave of absence. He returned to work for a year and a half before his health forced him to take more time off. He told his employees in August, "I have always said if there ever came a day when I could no longer meet my duties and expectations as Apple's CEO, I would be the first to let you know. Unfortunately, that day has come."

Flags fly at half-staff at Apple's headquarters in Cupertino, Calif.
(Credit: Daniel Terdiman/CNET) One of the most legendary businessmen in American history, Jobs turned three separate industries on their head in the 35 years he was involved in the technology industry.
Personal computing was invented with the launch of the Apple II in 1977. Legal digital music recordings were brought into the mainstream with the iPod and iTunes in the early 2000s, and mobile phones were never the same after the 2007 debut of the iPhone. Jobs played an instrumental role in the development of all three, and managed to find time to transform the art of computer-generated movie-making on the side.
The invention of the iPad in 2010, a touch-screen tablet computer his competitors flocked to reproduce, was the capstone of his career as a technologist. A conceptual hybrid of a touch-screen iPod and a slate computer, the 10-inch mobile device was Jobs' vision for a more personal computing device.
Jobs was considered brilliant yet brash. He valued elegance in design yet was almost never seen in public wearing anything but a black mock turtleneck, blue jeans, and a few days worth of stubble. A master salesman who considered himself an artist at heart, Jobs inspired both reverence and fear in those who worked for him and against him, and was adored by an army of loyal Apple customers who almost saw him as superhuman.
Jobs was born in San Francisco in 1955 to young parents who gave him up for adoption. Paul and Clara Jobs gave him his name, and moved out of the city in 1960 to the Santa Clara Valley, later to be known as Silicon Valley. Jobs grew up in Mountain View and Cupertino, where Apple's headquarters is located.
He attended Reed College in Oregon for a year but dropped out, although he sat in on some classes that interested him, such as calligraphy. After a brief stint at Atari working on video games, he spent time backpacking around India, furthering teenage experiments with psychedelic drugs and developing an interest in Buddhism, all of which would shape his work at Apple.
Back in California, Jobs' friend Steve Wozniak was learning the skills that would change both their lives. When Jobs discovered that Wozniak had been assembling relatively (for the time) small computers, he struck a partnership, and Apple Computer was founded in 1976 in the usual Silicon Valley fashion: setting up shop in the garage of one of the founder's parents.
Wozniak handled the technical end, creating the Apple I, while Jobs ran sales and distribution. The company sold a few hundred Apple Is, but found much greater success with the Apple II, which put the company on the map and is largely credited as having proven that regular people wanted computers.
It also made Jobs and Wozniak rich. Apple went public in 1980, and Jobs was well on his way to becoming one of the first tech industry celebrities, earning a reputation for brilliance, arrogance, and the sheer force of his will and persuasion, often jokingly referred to as his "reality-distortion field."
The debut of the Macintosh in 1984 left no doubt that Apple was a serious player in the computer industry, but Jobs only had a little more than a year left at the company he founded when the Mac was released in January 1984.
By 1985 Apple CEO John Sculley--who Jobs had convinced to leave Pepsi in 1983 and run Apple with the legendary line, "Do you want to spend the rest of your life selling sugared water or do you want a chance to change the world?"--had developed his own ideas for the future of the company, and they differed from Jobs'. He removed Jobs from his position leading the Macintosh team, and Apple's board backed Sculley.
Steve Jobs: A life in technology
He went on to found NeXT, which set about making the next computer in Jobs' eyes. NeXT was never the commercial success that Apple was, but during those years, Jobs found three things that would help him architect his return.
The first was Pixar. Jobs snapped up the graphic-arts division of Lucasfilm in 1986, which would go on to produce "Toy Story" in 1995 and set the standard for computer-graphics films. After making a fortune from Pixar's IPO in 1995, Jobs eventually sold the company to Disney in 2006.
The second was object-oriented software development. NeXT chose this development model for its software operating systems, and it proved to be more advanced and more nimble than the operating system developments Apple was working on without Jobs.
The third was Laurene Powell, a Stanford MBA student who attended a talk on entrepreneurialism given by Jobs in 1989 at the university. The two wed in 1991 and eventually had three children; Reed, born in 1991, Erin, born in 1995, and Eve, born in 1998. Jobs has another daughter, Lisa, who was born in 1978, but Jobs refused to acknowledge he was her father for the first few years of her life, eventually reconciling with Lisa and her mother, his high-school girlfriend Chris-Ann Brennan.
Jobs returned to Apple in 1996, having convinced then-CEO Gil Amelio to adopt NeXTStep as the future of Apple's operating system development. Apple was in a shambles at the time, losing money, market share, and key employees.
Flowers sit near a sign at Apple headquarters in Cupertino, Calif.
(Credit: Daniel Terdiman/CNET)By 1997, Jobs was once again in charge of Apple. He immediately brought buzz back to the company, which pared down and reacquired a penchant for showstoppers, such as the 1998 introduction of the iMac; perhaps the first "Stevenote." His presentation skills at events such as Macworld would become legendary examples of showmanship and star power in the tech industry.
Jobs also set the company on the path to becoming a consumer-electronics powerhouse, creating and improving products such as the iPod, iTunes, and later, the iPhone and iPad. Apple is the most valuable publicly-traded company in the world, surpassing ExxonMobil's market capitalization in August. He did so in his own fashion, imposing his ideas and beliefs on his employees and their products in ways that left many a career in tatters. Jobs enforced a culture of secrecy at Apple and was an extremely demanding leader, terrorizing Apple employees when he returned to the company in the late 1990s with summary firings if he didn't like the answers they gave when questioned.
Jobs was an intensely private person. That quality put him and Apple at odds with government regulators and stockholders who demanded to know details about his ongoing health problems and his prognosis as the leader and alter ego of his company. It spurred a 2009 SEC probe into whether Apple's board had made misleading statements about his health.
In the years before he fell ill in 2008, Jobs seemed to soften a bit, perhaps due to his bout with a rare form of pancreatic cancer in 2004.
In 2005, his remarks to Stanford graduates included this line: "Remembering that I'll be dead soon is the most important tool I've ever encountered to help me make the big choices in life. Because almost everything--all external expectations, all pride, all fear of embarrassment or failure--these things just fall away in the face of death, leaving only what is truly important."
Later, in 2007, he appeared onstage at the D: All Things Digital conference for a lengthy interview with bitter rival Bill Gates, exchanging mutual praise and prophetically quoting the Beatles: "You and I have memories longer than the road that stretches out ahead."
Jobs leaves behind his wife, four children, two sisters, and 49,000 Apple employees.
Tom Krazit, Erica Ogg, and Josh Lowensohn wrote this report.

A bagpiper plays at Apple headquarters.
Saturday, October 1, 2011
Reports: Microsoft Anti-Virus Erasing Google Chrome
 Mighty funny timing, Microsoft. Reports say that Google’s Chrome browser was threatening to overtake Firefox in the coming months thanks to soaring usage rates caused, in large part, by FF and IE defectors. Then, this morning, Internet forums are awash with rage because a new update to Microsoft’s Security Essentials and ForeFront AV software began calling Chrome a Trojan and erasing it from users machines. Coincidence? Yeah, it probably is. But that still doesn’t change the fact that users are pissed.
Mighty funny timing, Microsoft. Reports say that Google’s Chrome browser was threatening to overtake Firefox in the coming months thanks to soaring usage rates caused, in large part, by FF and IE defectors. Then, this morning, Internet forums are awash with rage because a new update to Microsoft’s Security Essentials and ForeFront AV software began calling Chrome a Trojan and erasing it from users machines. Coincidence? Yeah, it probably is. But that still doesn’t change the fact that users are pissed. Both ZDNet and The Register are reporting that they’ve received numerous complaints about the critical false positive. The AV programs are identifying Chrome as part of the ZeuS Trojan, and users who try to reinstall the browser are finding that the antivirus program won’t let them, citing “PWS:Win32/Zbot” as a severe threat. Register readers are reporting that the beta version of Chrome isn’t affected, nor are browsers that are configured to not send Google any information. Nobody’s saying anything official at the moment – both Google and Microsoft have been mum on the matter.
So, has any of you been affected by the bug? Chime in with your experiences in the comments! I've got Chrome and MSE installed on my laptop, and nothing fishy has gone on yet.
Labels:
Antivirus,
Aryan Gupta,
Aryan.Born To Hack,
Aryan.Master Of All Hackig Warez,
Born To Hack,
Free,
Google,
Google Chrome,
Master Of All Hackig Warez,
Microsoft,
Security,
Tech News
Cisco's Android-based tablet 'Cius' comes to India
Networking solution provider Cisco has forayed into the Indian tablet market with the launch of 'Cius' and is eying the enterprise segment for its new product. Cisco's new device is priced at Rs. 35,000 and with docking station, it will cost around Rs. 50,000.
The company says it is focussing on its existing customers and subscribers of its IP telephony services, which are nearly 700,000 in India. "Cius is not just another tablet. It has more to do with providing applications helping productivity in a secure environment," says Cisco official Minhaj Zia.

The Cius tablet runs on Android 2.2 operating system and is powered by a 1.6 GHz Intel Atom Processor. The device has a seven-inch display and comes with 1GB RAM and an expandable memory up to 32GB. The Cius has dual cameras (frontal and 5MP rear) and for connectivity, it supports Bluetooth 3.0, 3G/4G and WiFi. Check out our previous coverage on the Cius tablet here.
Following the footsteps of other players such as LG, HTC and Samsung, Cisco has incorporated its own app store called Cisco AppHQ in the device. The company says access to Cisco AppHQ and Android Market will assist companies selecting 'secure' mobile business-differentiated apps.
The Indian market is presently flooded with tablets from companies like Apple, Samsung, HTC, RIM and several others. Of late we have seen a number of tablet launches from different companies. The competition is stiffening with the advent of low-cost tablets such as Reliance 3G Tab and Beetel Magiq.
According to analysts, the tablet PC segment in India is likely to continue grow with sales touching one million units over the next 12 months.
Friday, September 30, 2011
How to Enable Facebook Timeline just in Few Seconds
 Sone days back Facebook announced Timeline, a crazy (and kind of creepy) omnibus look at everything that has ever happened in your Facebook lifespan. It’s like a story book of your life — or at least the online, documented parts.
Sone days back Facebook announced Timeline, a crazy (and kind of creepy) omnibus look at everything that has ever happened in your Facebook lifespan. It’s like a story book of your life — or at least the online, documented parts. Facebook said that Timeline would be on the way for everyone sometime in the coming weeks… which is great and all, for everyone else. You’re the type of person who reads Borntohack, and are thus likely the type of person who likes their new and shiny things right now.
That’s okay. We can make it happen.
Fortunately, enabling Timeline a bit early isn’t too difficult — but it’s not at all straight forward, either.
You see, Facebook is enabling Timeline early for open graph developers. You, too, can be an open graph developer — even if you’re just looking to dabble.
A few things to note:
- You probably don’t want to do this unless you’re actually a developer. Expect bugs.
- Only you will see your timeline at first (unless you decide otherwise), but it will automatically go public after a few days. My timeline was automatically hard-set to go public on September 29th.
- It seems that if you login into Facebook on another machine, Timeline gets disabled automatically on all of your machines. With that said, it seems you can get back to your timeline (but ONLY after following the steps below) by navigating to http://www.facebook.com/YOURUSERNAMEHERE?sk=timeline
- You’ll need to have a “verified” account for one of the steps, which means you need a credit card or phone number attached to the account.
Here’s how to do it:
1. Log into Facebook
2. Enable developer mode, if you haven’t already. To do this, type “developer” into the Facebook search box, click the first result (it should be an app made by Facebook with a few hundred thousand users), and add the app.

3. Jump into the developer app (if Facebook doesn’t put you there automatically, it should be in your left-hand tool bar)
4. Create a new app (don’t worry — you
Labels:
Aryan Gupta,
Aryan.Born To Hack,
Aryan.Master Of All Hackig Warez,
Born To Hack,
Facebook,
Facebook Timeline,
Free,
Master Of All Hackig Warez,
New,
Tech News,
Tricks And Tips
Sunday, September 25, 2011
No, Facebook Will Never Demand Money from you to Get New Profiles

A completely untrue rumor that Facebook will soon start charging users is making the rounds yet again.
Ever since Facebook introduced Timeline profiles, several Facebook status updates have been spreading on the world’s social network that claim Facebook users will have to pay for the new profile changes.
Here’s one of the messages currently spreading on Facebook:
“THIS IS OFFICIAL… IT WAS EVEN ON THE NEWS… FACEBOOK WILL START CHARGING DUE TO THE NEW PROFILE CHANGES… IF YOU COPY THIS ON YOUR WALL YOUR ICON WILL TURN BLUE AND FACEBOOK WILL BE FREE FOR YOU. PLEASE PASS THIS MESSAGE ON, IF NOT YOUR ACCOUNT WILL BE DELETED IF YOU DO NOT PAY!!”
And here’s yet another:
“FACEBOOK JUST RELEASED THEIR PRICE GRID FOR MEMBERSHIP. $9.99 PER MONTH FOR GOLD MEMBER SERVICES, $6.99 PER MONTH FOR SILVER MEMBER SERVICES, $3.99 PER MONTH FOR BRONZE MEMBER SERVICES, FREE IF YOU COPY AND PASTE THIS MESSAGE BEFORE MIDNIGHT TONIGHT. WHEN YOU SIGN ON TOMORROW MORNING YOU WILL BE PROMPTED FOR PAYMENT INFO…IT IS OFFICIAL IT WAS EVEN ON THE NEWS. FACEBOOK WILL START CHARGING DUE TO THE NEW PROFILE CHANGES”
These rumors are simply untrue. “It’s free and always will be” is still in giant font on the Facebook homepage.
Subscribe to:
Posts (Atom)

Stuffs
- Android (12)
- Antivirus (3)
- Backtrack (13)
- Borntohack News (5)
- Cracking (6)
- Ethical Hacking (17)
- Facebook (47)
- Filesonic Premium Accounts (3)
- Firefox (34)
- Google (66)
- Google+ (8)
- Hacking (220)
- Hotfile Premium Accounts (1)
- IPod Stuff (38)
- Linux (7)
- Metasploit (2)
- Mobile Stuff (48)
- Registry Hacks (43)
- Security (106)
- Tech News (182)
- Tricks And Tips (512)
- Trojan (5)
- Unlocking (2)
- Windows (68)
- Yahoo (5)
- cydia (2)
- hacking tools (4)
- iOS4 (11)
- iOS5 (6)
- iPad (25)
- iPhone (55)
- javascript (23)
Facebook :
Translate Website
Follow On Buzz
Hacking Purity Test Solutions
Subscribe Email :
Blog Archive
-
▼
2013
(50)
-
▼
July
(10)
- C PROGRAM TO SHUT DOWN COMPUTER
- History Behind Name of Apple
- History Behind Name of Google
- History Behind Name OF Microsoft
- History Behind Name of Yahoo
- History Behind Name of Intel
- If you don't want Facebook, Google, Gmail to track...
- Disable Delete Confirmation
- 12 Computer Programming Languages You're Probably ...
- Earn Mobile Recharges and gifts by bidding online.
-
▼
July
(10)
Discussion Here ..!!!
SMS Subscribe
Security Alerts
Pages
Total Pageviews
Network Blogs
Get Domain Here :-
All Rights Reserved. http://borntohack.in Designed By Shaify Mehta








